Hyper Elliptic Curve Based Certificateless Signcryption Scheme for Secure IIoT Communications
2022-08-24UsmanAliMohdYamaniIdnaIdrisJaroslavFrndaMohamadNizamBinAyubRoobaeaAlroobaeaFahadAlmansourNuraModiShagariInsafUllahandIhsanAli
Usman Ali,Mohd Yamani Idna Idris,Jaroslav Frnda,Mohamad Nizam Bin Ayub,Roobaea Alroobaea,Fahad Almansour,Nura Modi Shagari,Insaf Ullah and Ihsan Ali
1Department of Computer System and Technology,Faculty of Computer Science and Information Technology,University of Malaya,Kuala Lumpur,50603,Malaysia
2Department of Computer Science,University of Swat,Saidu Sharif,19130,Pakistan
3Center for Research in Mobile Cloud Computing,University of Malaya,Kuala Lumpur,50603,Malaysia
4Department of Quantitative Methods and Economic Informatics,Faculty of Operation and Economics of Transport and Communications,University of Zilina,010 26 Zilina,Slovakia
5Department of Computer Science,College of Computers and Information Technology,Taif University,Taif,21944,Saudi Arabia
6Department of Computer Science,College of Sciences and Arts in Rass,Qassim University,Buraydah,51452,Saudi Arabia
7Department of Computer Science,Hamdard Institute of Engineering and Technology,Islamabad,44000,Pakistan
Abstract:Industrial internet of things(IIoT)is the usage of internet of things(IoT) devices and applications for the purpose of sensing, processing and communicating real-time events in the industrial system to reduce the unnecessary operational cost and enhance manufacturing and other industrial-related processes to attain more profits.However, such IoT based smart industries need internet connectivity and interoperability which makes them susceptible to numerous cyber-attacks due to the scarcity of computational resources of IoT devices and communication over insecure wireless channels.Therefore, this necessitates the design of an efficient security mechanism for IIoT environment.In this paper, we propose a hyperelliptic curve cryptography(HECC)based IIoT Certificateless Signcryption(IIoT-CS) scheme, with the aim of improving security while lowering computational and communication overhead in IIoT environment.HECC with 80-bit smaller key and parameters sizes offers similar security as elliptic curve cryptography(ECC)with 160-bit long key and parameters sizes.We assessed the IIoT-CS scheme security by applying formal and informal security evaluation techniques.We used Real or Random(RoR)model and the widely used automated validation of internet security protocols and applications(AVISPA) simulation tool for formal security analysis and proved that the IIoT-CS scheme provides resistance to various attacks.Our proposed IIoT-CS scheme is relatively less expensive compared to the current state-of-the-art in terms of computational cost and communication overhead.Furthermore, the IIoT-CS scheme is 31.25% and 51.31% more efficient in computational cost and communication overhead,respectively,compared to the most recent protocol.
Keywords: IoT security; authentication protocols; hyperelliptic curve cryptography; certificateless public key cryptography
1 Introduction
The Internet of Things (IoT) is a rapidly evolving infrastructure which allows traditional systems to connect with one another by incorporating new devices such as sensors, actuators, and other smart devices.The integration of IoT and wireless sensor networks (WSN) has boosted the usage of IoT in our everyday lives, such as health tracking, smart houses, smart cities, and smart transportation [1].The widespread use of IoT can also be seen in an industrial environment known as Industrial IoT (IIoT) or Industry 4.0, including industrial automation, aviation, smart retail, smart farming, and power systems [2–4].The IIoT refers to the use of well-connected IoT devices for collecting and communicating real-time events in industrial systems to reduce human effort and operational costs and to enhance manufacturing and industrial processes.However,these interconnected smart devices and networks have been used to enable a variety of cyberattacks due to the inadequate computational resources and communication over insecure wireless channels.Therefore, this necessitates the design of an efficient and secure mechanisms for IIoT environment.The limited battery life of smart devices is one of the main obstacles in the design of security solutions for IIoT applications.As a result, a current research focus is on developing a secure and efficient solutions for resource-constrained IoT devices.The security requirements for IIoT data, such as confidentiality, integrity, authenticity, and non-repudiation must always be ensured due to the resource-constrained IoT devices and communications over an insecure network.A signature-then-encryption mechanism is one solution to ensure such security requirements, however, this approach is not appropriate for low computing IoT devices as it produces the message’s signature and encryption in two separate steps.To enhance the performance, Zheng [5]introduced Signcryption techniques, which incorporates signature and encryption in a single logical step.However, Zheng approach is based on public key cryptography (PKC).In PKC based schemes, the public key of a participating entity contains a random number belonging to some group that does not offer authenticity to the participating entity as the group elements provide no identity to the participating entities [6].To address the flaws in PKC based schemes, the notion of public key infrastructure (PKI) was introduced in which a certificate authority (CA) is used that binds the public key with certificates [7].However, this mechanism suffers from certificate storage, distribution, and manufacturing difficulties [8].To overcome these shortcomings, the idea of identity-based cryptography (IBC) was suggested in [9].IBC enables the participating entities to produce public keys directly from their identities, such as e-mail and phone numbers, without the need for CA, and the private key for each participating entity is generated by the trusted server which acts as the key generation center (KGC).The principle Signcryption was implemented to merge the features of signature and encryption into a single step [10].However, IBC based schemes suffer from the key escrow problem in which the KGC has the complete knowledge of the private keys of all participants.To address this problem, the idea of Certificateless Public Key Infrastructure (CPKI) was suggested in [11].In CPKI, a participant’s private key is made up of two parts:one part is the private key provided by the KGC, and the second part is a secret value generated by the participant itself.The concept of Certificateless Signcryption (CS)was introduced, in which the principle of Signcryption was implemented to merge the features of signature and encryption into a single step [12].
Normally, the above-mentioned Signcryption schemes’security and efficiency depend on some computationally difficult problems, for instance, RSA, bilinear pairing (BP), and elliptic curve cryptography (ECC).The RSA [13,14] scheme is not appropriate for resource constraint devices because it contains large factorization and uses a 1024-bit large key size [15].Furthermore, BP is 14.31 times worse than RSA [16].ECC has been introduced to address the shortcomings of RSA and BP [17].In comparison to BP and RSA, ECC uses less parameter size, public key, and private key sizes.Furthermore, the efficiency and security of the ECC is based on 160-bit key size [18].However, ECC based schemes are still inefficient for resource constraint IoT devices.To enhance the efficiency of ECC based schemes, the idea of hyper elliptic curve cryptography (HECC) was introduced [19].The HECC offers the similar level of security as ECC by utilizing 80-bit small key sizes [20–22].Thus, HECC is considered a better choice for resource constraint IoT devices.In this paper, we proposed HECC based IIoT certificateless Signcryption (IIoT-CS) scheme for secure communication in IIoT environment.
1.1 Motivation and Contributions
Recently, Garg et al.[23] Proposed authentication scheme for IIoT environment.We found that their scheme is based on a hierarchical approach in which two participating IoT nodes cannot perform mutual authentication directly without an active server.In their scheme, the intended IoT nodes need to perform an authentication process with the server before they start communication,which increases the communication overhead for each IoT node.Furthermore, the efficiency and security of their scheme is based on ECC which suffer from high computational overhead due to the large parameters and key sizes compared to HECC.Their scheme’s verification is not proved using formal security verification tools such as RoR.To address these shortcomings, we propose HECC based IIoT-CS scheme for secure IIoT communications.As we mentioned in the introduction, the HECC offers a similar level of security as ECC, RSA, and bilinear pairing by using a smaller key size, which reduces the computational and communication overhead.We verified the security of IIoT-CS scheme using the RoR model and AVISPA simulation tool.We also performed the informal security analysis of the proposed scheme.Furthermore, the results proved the efficiency of IIoT-CS scheme.
1.2 Outline of the Paper
The remainder of the paper is presented as follows.Section 2 contains related work; Section 3 shows the system model and threat models; Section 4 presents the proposed scheme; Section 5 demonstrates the proof of correctness; Section 6 presents the security evaluation; Section 7 presents the comparative analysis; Section 8 discusses the conclusion and finally Section 9 shows future work.
2 Related Work
Information security is important to protect critical information in modern communication systems where the communication is held through an insecure public networks.The research community is also echoing the significance of such a topic [24–26].Hassija et al.[27] addressing the evolving security issues in IoT environments, emphasizing the significance of maintaining secure communication among IoT nodes.To safeguard sensitive data/information, it must be concealed from unauthorized access (confidentiality), identify who sent the message (authentication),be protected from alteration (integrity), and be available to a legitimate user [28].Therefore,encryption techniques are used to ensure confidentiality, whereas digital signatures are applied to guarantee integrity and authenticity.In the conventional encryption mechanism known as signature-then-encryption in which the sender has to first sign and then encrypt the data.However,this approach has some drawbacks, such as requiring more machine cycles and energy, which reduces the performance.To address these shortcomings, the concept of Signcryption was introduced in [5].However, this approach is based on PKC in which the public key of a participating entity contains a random number belonging to some group that does not offer authenticity to the participating entity as the group elements provide no identity to the participating entities [6].To address Signcryption flaws in [5], IBS scheme were suggested in [10].However, it turned out that IBS scheme suffer from the key escrow problem.To address this issue, CS scheme was introduced in [12].Following this scheme, another CS scheme based on random oracle model (ROM) was proposed [29].Wahid et al.[30] proposed EC-based CS efficient scheme.Zhou et al.[31] proposed a new SM based CS scheme.They used the modified decisional bilinear Diffie Hellman problem and square computational Diffie Hellman problem to prove their scheme’s security requirements.Rastegari et al.[32] proposed SM based CS scheme.Yu et al.[33] proposed a new CS scheme and demonstrated their scheme’s security by using ROM.Lin et al.[34] presented the cryptanalysis of the of scheme in [33] and found that since the requirements of confidentiality and unforgeability are not fulfilled, their scheme may be completely thwarted.Zhou [35] suggested a new BP based CS scheme using SM for security proof.
3 System and Threat Model
This section shows the details of the system model and threat model considered for the proposed IIoT-CS scheme.
3.1 System Model
Primarily, an IIoT environment consists of multiple IoT domains made up of IoT devices called nodes such as sensors, actuators, and other devices as shown in Fig.1.These IoT devices routinely collect information and transmit it to other devices in the network.The focus of this article is to design an authentication schemes to secure the communication among IoT nodes.The IoT nodes have minimal computing resources, while the KGC is a trusted server which has ample resources.We further assume that certain cryptographic elements are preloaded into the memory of all participating nodes and the nodes have to transmit their public keys and identities to KGC and other nodes to which they want to communicate.
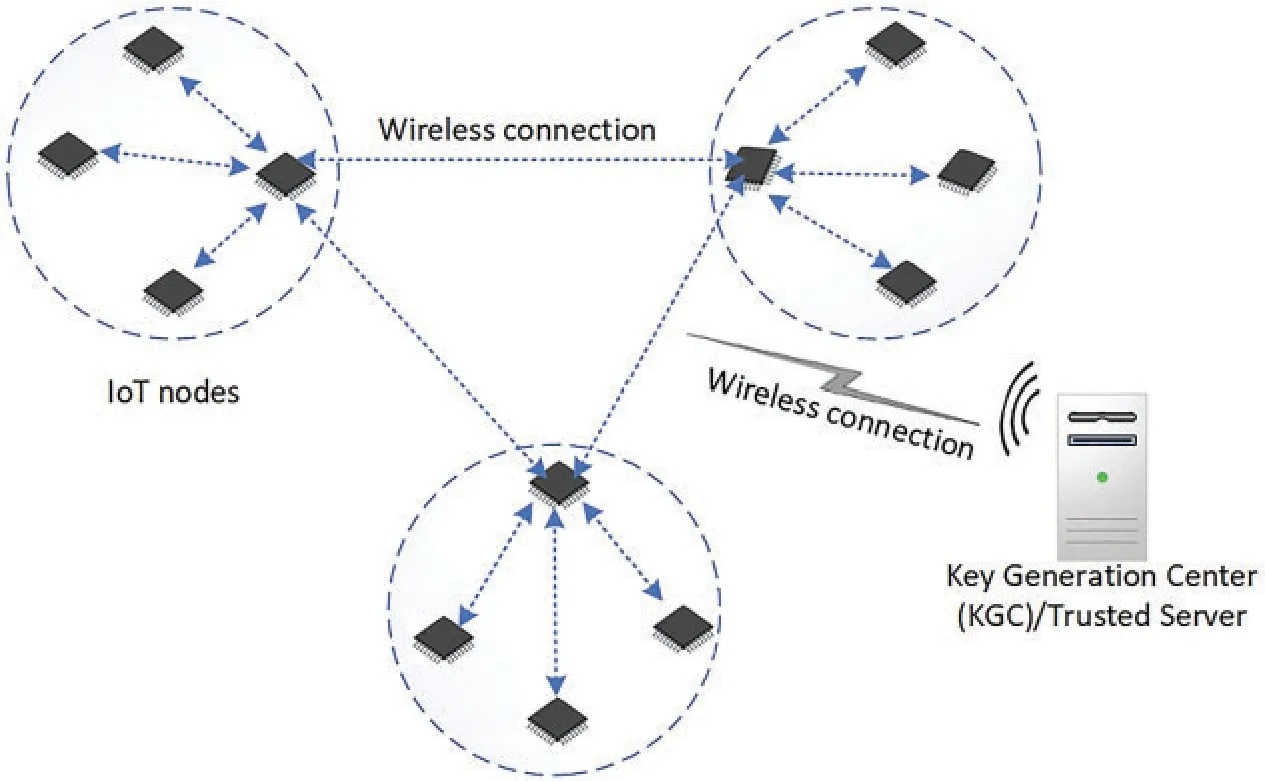
Figure 1:System model of the proposed scheme
3.2 Threat Model
In the proposed scheme, we considered a powerful threat model called Dolev-Yao (DY)threat model [36], which allows an adversary to execute passive and active attacks.According to DY threat model, the adversary has access to the communication network and can listen in to all communications between participating entities.Furthermore, the adversary has complete knowledge of all public parameters of participants in the system, however the adversary has no access to the participant’s private data.Furthermore, the adversary can impersonate any device in the system by replaying messages previously eavesdropped from the communication channel.
4 Proposed Scheme
The proposed IIoT-CS scheme is based on HEC certificateless Signcryption and involves two phases, namely:pre-deployment phase and authentication phase, as shown in Fig.2.The notations used in the proposed IIoT-CS scheme are shown in Tab.1.

Figure 2:Flow of interaction in the proposed IIoT-CS scheme
4.1 Pre-Deployment Phase
The predeployment phase is performed by the system administrator before the effective deployment of the system.In this phase, the IoT nodes are equipped with the basic cryptographic parameters necessary to establish secret session keys.This process is divided into two parts,namely, the system initialization stage and the registration stage.

Table 1:Notations used in the proposed IIoT-CS scheme
4.1.1 System Initialization Phase
This process is carried out by the KGC, during which the following cryptographic information are initialized and made public.
i) The hyperelliptic curveE/Fqover a prime finite fieldFq.
ii) The algebraic closuref*ofFq.
iii) The Divisor groupDof the curveE.
iv) Hashing functionH:{0, 1} →, where, = {1, 2,..., q - 1}
In addition, the KGC generates its master private keyVs∈Rand master public keyUs=Vs.D.Finally, it makes the public parametersparams= {Fq,f*,q,x,y,D,Us,H}, publicly available to all participants.
4.1.2 Registration Phase
During the registration stage, the system’s IoT nodes communicate with the KGC across a secure network in order to obtain dedicated cryptographic components.During the registration stage, the IoT nodes participating in the system communicate with the KGC through a secure communication channel to register their self and receive dedicated cryptographic information from the KGC.The flow of interaction of IoT nodes with the KGC is described below and shown in Fig.2.
Step 1:The intended IoT node (sayith-node), that requires to be registered with the KGC,generates its identityIDiand private key as Vi∈R.Next, the node computes the first part of its public key asUi=Vi.D.The node then, computes a stringWi=(IDi||Ui), and transmits it to the KGC using a secure channel.
Step 2:Upon receiving {Wi}, the KGC performs the following operations to compute the corresponding second part of the private and public keys on behalf ofith-node.
i) The KGC selects a random value ri∈R, compute Yi=ri.D and sets it as the second part of the public key of theith-node.
ii) The KGC computes hi=H(Wi||Yi) and Xi=((ri+hi.Vs) mod q) and sets Xias the second part of the private key of theith-node.The KGC delivers Xiand Yito theith-nodeusing a secure channel.
Step 3:Upon receiving the second part of its private and public keys from KGC, theith-nodecan verify the authenticity of these keys by using the equation Xi.D=Yi+hi.Us.If this equation is validated, then the keys could be deemed valid and correctly generated by the KGC.Thus, theith-nodecan set its full private key as (Vi, Xi) and full public key as (Ui, Yi).
4.2 Authentication Phase
The authentication process is initiated by an IoT node (sayith-node) with the intention of communicating with the other IoT nodes (sayjth-node) as depicted in Fig.2.As described in the predeployment phase, each IoT node is preloaded with certain cryptographic information.Furthermore, to begin the authentication process, theith-nodegenerate a messageM1=〈Wi, Yi〉and transmit it to thejth-node.On receivingM1 thejth-nodereplies with a new messageM2=〈Wj, Yj〉.On receivingM2 from thejth-node, theith-nodegenerates a fresh session key, ciphertext,and signature by using the certificateless Signcryption operation as described below.
i) Generate a timestamp Ti, select a fresh nonce ni∈{1,2,3,...,q-1}and a random secret valueb∈{1,2,3,...,q-1}and computeZ=b.D.
ii) Computeα=Yj+US.H(Wj||Yj)
iii) Compute a secret session keySK=b(Uj+α)
iv) Compute cipher text C=ESK(IDi,m,ni), where m is plaintext.
v) Computes the digital signatureS=(Xi+H(IDi||m||ni)(Vi+b)) mod q
vi) Theith-nodesendsM3=〈Ti,C,S,Z〉to thejth-nodeusing insecure channel.
On receiving M3, thejth-nodecheck the validity of Tiand if it is found to be valid, then proceed with the authentication procedure, otherwise terminate the session.Thejth-nodevalidates the digital signature and decrypt the ciphertext by using certificateless Un-Signcryption operation as described below.
i) Computes the secret session keySK′=Z(Vj+Xj)
ii) Perform decryption operation DSK′ (C)= (IDi,m,ni)
iii) computeβ=Yi+US.H(Wi||Yi)
iv) if S.D=β+H (IDi||m||ni). (Z+Ui) is hold, thenith-nodeis authenticated successfully.
Thejth-nodeComputeKij=Vj.Uiand compute the messageAuth=H(Wi⊕Wj⊕ni⊕Kij).
Finally, thejth-nodegenerate time stamp Tjand send the messageM4=〈Tj,Auth〉 to theith-node.Theith-nodeafter receiving M4 from thejth-node, first validate Tjand if it is found to be valid, then proceed with the authentication procedure, otherwise terminate the session.
Theith-nodecomputeKji=Vi.UjandAuth′=H(Wi⊕Wj⊕ni⊕Kji).
IfAuth=Auth′, then thejth-nodeis authenticated successfully.
5 Proof of Correctness
This section presents the proof of the correctness of the secret session key and signature verification.
5.1 Proof of Secret Session Key SK′=SK
SK′=Z(Vj+Xj),where Z=b.D and Xj=rj+Vs.H(Wj||Yj)
⇒b.D(Vj+rj+Vs.H(Wj||Yj))
⇒b.Vj.D+b.rj.D+b.Vs.D.H(Wj||Yj)
⇒b(Vj.D+rj.D+Vs.D.H(Wj||Yj)), whereUj=Vj.D,Yj=rj.D, andUs=Vs.D
⇒b(Uj+Yj+Us.H(Wj||Yj)), whereα=Yj+Us.H(Wj||Yj)
⇒b(Uj+α)=SKhence proof of correctness is verified.
5.2 Proof of Signature Verification
β+(Z+Ui)H(IDi||m||ni)=S.D
β+ (Z+Ui).H(IDi||m||ni), whereβ=Yi+Us.H(Wi||Yi)
⇒Yi+Us.H(Wi||Yi)+ (Z+Ui).H(IDi||m||ni)
⇒Yi+Us.H(Wi||Yi)+Z.H(IDi||m||ni)+Ui.H(IDi||m||ni), where Yi=ri.D,Us=Vs.D,Z=b.Dand Ui=Vi.D
⇒ri.D+Vs.D.H(Wi||Yi)+b.D.H(IDi||m||ni)+Vi.D.H(IDi||m||ni)
⇒ (ri+Vs.H(Wi||Yi)+(b+Vi).H(IDi||m||ni))D, where Xi=ri+Vs.H(Wi||Yi)
⇒ (Xi+(b+Vi).H(IDi||m||ni))D, whereS=Xi+(b+Vi).H(IDi||m||ni)
⇒S.D, hence correctness of digital signature is verified.
6 Security Evaluation
We conducted both formal and informal security assessments to illustrate the potential of the IIoT-CS scheme against various attacks.The two computational problems that are useful in performing the formal security analysis are described below.
Definition 1:Collision-Resistant One-Way Hash Function (H (.):{0,1}*→{0,1}n)
It is a “deterministic mathematical function that accepts a variable-length input string and produces a n-bit fixed-length output string”.
Definition 2:(Hyper Elliptic Curve Discrete Logarithm Problem (HECDLP))
According to HECDLP, it is infeasible for an attacker to extract a value j from the relationL=j.D, whereas j ∈is the random number from= {1, 2,..., q - 1}.
6.1 Formal Security Analysis Using RoR Model
We used ROR model [37] in which an adversary simulates real attacks to target the communication between IoT nodes.In the proposed IIoT-CS scheme, an adversary is represented byAdand the participating nodes are represented byith-nodeandjth-node.Further, we assume the instances ofith-nodeandjth-nodeare represented byΦ= {Φi andΦj}.Adinitiates the following queries to interact withΦ.
i)Execute query:Adeavesdrops on the communication channel and intercepts all communication betweenΦ.
ii)Send query:Adtransmits a message toΦand obtains a reply from it consequently.
iii)Reveal query:Adattempts to recover the session key betweenΦi andΦj.
iv)Test query:AdrequestsΦfor session key and it responds with a random bit c.
Moreover, H(.) is modeled as a random oracle which is available to all participants and adversaryAd.In the proposed IIoT-CS scheme, we demonstrated the existence of session key security (semantic security) by using Theorem 1 as stated below.
Theorem 1:AssumeAdruns in a polynomial timeptand attempts to break the session key security betweenΦi and nodeΦj thenAd’s advantage in breaching the session key security can be written as follows:

where the variables |Hash|,, and(pt) represent the range space of H(.), the number of hash queries, and the non-negligible winning advantage of breaking HECDLP respectively.
Proof of Theorem 1:To prove Theorem 1, we used three GamesGi(i=1,2,3).Within each gameGi,Adattempts to guess the bitcby applying the test query.If, is an event whereAdaccurately guessesc, soAd’s advantage is as follows:

Game G1:This game is similar like the real scheme that runs in RoR model.We obtain the following result in this game.

Game G2:InG2, Ad intercepts all messages exchanged betweenΦi andΦj, these messages arem1={Wi, Yi}, m2={Wj, Yj}, m3={C, R, S, Z}andm4={Auth}.Next,Ademploys the Execute query to retrieve the session key, then employs the Reveal and Test queries to examine if the obtained session key is original or randomly generated.In the proposed IIoT-CS scheme, the session key can be produced asSK=b(Uj+α)=SK′=Z(Vj+Xj).To obtain this key correctly,Adneeds the secret valuesb,VjandXj.It implies that just eavesdropping of m1, m2, m3, and m4 would not improveAd’s winning probability.Hence, G1 and G2 are indistinguishable as shown in the following equation.

Game 3:This game makes use of the Send and Hash queries.InG2, we know that eavesdropping onm1,m2,m3, andm4betweenΦi andΦj, would not result in hash collision as these messages are safeguarded by HECDLP and hash function.HECDLP protects the variablesb,Vs, Vi, andVjused withinZ, Us, UiandUjrespectively, while the hash function protects the variable S and the encryption algorithm protects the variablesC, and Auth.Moreover,G2andG3are indistinguishable except G3 solves HECDLP and performs the Hash and Send queries.The advantage of solving HECDLP byAis(pt), and, as per the birthday paradox, using such a hash oracle query has a probability.Overall, the following result is obtained.
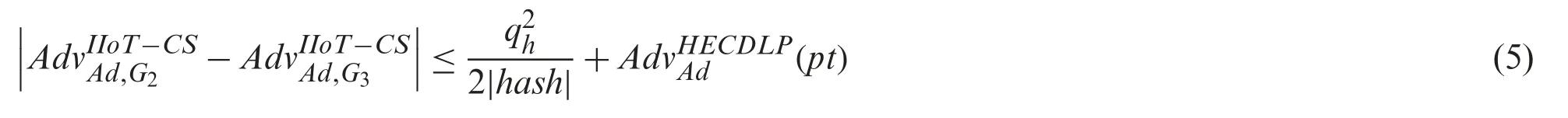
NowAdexecutes all queries and guessing the bitc, the following result is obtained

From Eqs.(3) and (4), we obtain the following result.

From Eqs.(6) and (7), we obtain the following result.

Similarly, from Eqs.(5) and (8), we obtain the following result.

Now multiplying Eq.(9) by “2” we obtain the following result.
6.2 Formal Security Verification Using AVISPA
We used AVISPA tool [38] to verify the proposed IIoT-CS scheme security towards known attacks.AVISPA gives the results by using the keywords SAFE, or UNSAFE, which denotes whether the protocol is secure or not secure against various attacks.We applied two backends of AVISPA simulation tool, namely:OFMC and CL-ATSe to verify the security of our scheme.The result show that the IIoT-CS scheme is secure against various attacks under the DY threat model as shown in Fig.3.
6.3 Informal Security Analysis
The following assumptions were taken into account for the informal security analysis.The secret values (b, Vs, Vi and Vj) are only known to the corresponding participating entity (KGC and IoT nodes) and the adversary has no knowledge about it.The encryption algorithm (ESK) is secure enough that an attacker cannot not decryptCand {Auth}.
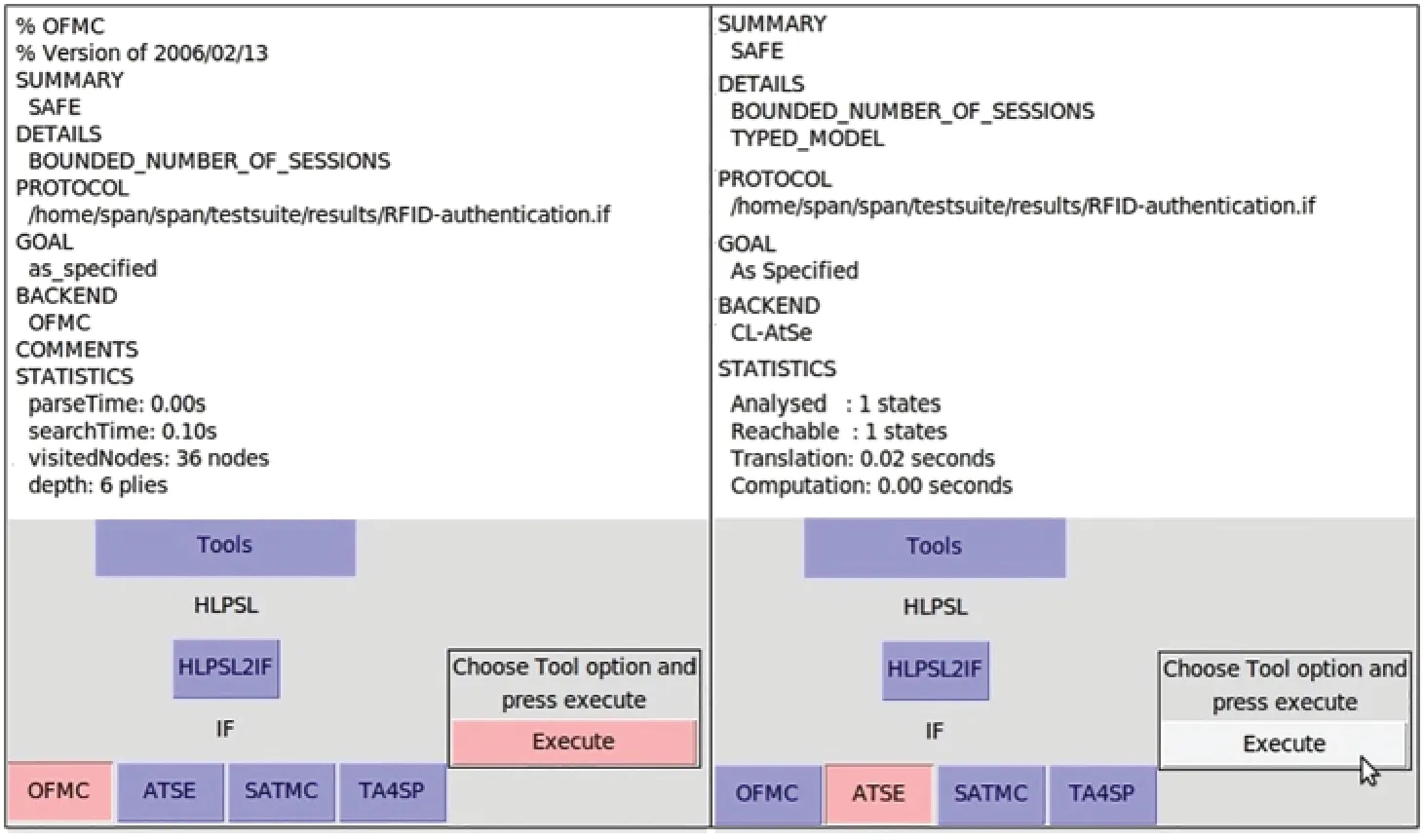
Figure 3:AVISPA simulation results for the proposed IIoT-CS scheme
6.3.1 Confidentiality
Confidentiality refers to the assurance that private information will be kept secret during transmission.In the start, theith-nodeandjth-nodeshare their public keys and identities in the form of plain text with each other because they are not required to be kept secret.Theith-node,then transmit the message {Ti, C, S, Z} to thejth-node.The time stampTiwhich discloses no information.The adversary cannot interpret the ciphertextCas it requires the secret session key SK which depends on the private random numberb.According to HECDLP, an adversary is unable to computebgivenZandD.Similarly,Adis unable to extract any knowledge from S because it depends on the private values (Viandb) ofith-node.The messages {Tj,Auth} sent by thejth-nodeto theith-nodealso reveals no information.Tjis the time stamp andAuthis a hash message in which an adversary cannot extract any information.As a result, the existing protocol successfully provides confidentiality features.
6.3.2 Authentication
To ensure secure communication between IoT nodes, they must authenticate each other at the start within each session and vice versa.
ith-nodeauthentication:Thejth-nodecalculates the session key SK after obtaining the message{C, S, Z} fromith-node.Thejth-nodeverify the signatureS= Xi+(b+Vi).H(IDi||m||ni)of theith-nodeby using the equationS.D=β+ (Z+Ui)H(IDi||m||ni).If this equation hold then theith-nodeis successfully authenticated by thejth-node.Suppose an adversary imitates to be a legitimate node, in that scenario, it would need to generate a valid S.However,Sis based on the private values ofith-nodewhich are only known to theith-nodeso any adversary would not be able to produce the right value of S.
jth-nodeauthentication:After receiving{Auth} from thejth-node, theith-nodecomputes{Auth′}.Theith-nodecheck ifAuth=Auth′, thenjth-nodeis successfully authenticated by theith-node.If an adversary pretends itself as a legitimate node, it must send the right message {Auth}.However,{Auth} is hashed message which is based on private key ofjth-node, making it difficult for an adversary to transmit the right message {Auth}.
6.3.3 Non-Repudiation
The value ofStransferred to thejth-nodeby theith-nodeis based on the private key ofithnode.Similarly, the message {Auth} sent by thejth-nodeto theith-nodeis based on the private key of thejth-node.If thejth-nodeverifiedith-nodesignature i.e., ifS.D=β+ (Z+Ui)H(IDi||m||ni)is hold, theith-nodewill not deny that it sent the message to thejth-node, and ifAuth=Auth′,thejth-nodewill not deny that it delivered the message to theith-node.
6.3.4 Integrity
The proposed scheme can verify that whether a cipher textCwas changed or not during the communication, by using the equationS.D=β+ (Z+Ui)H(IDi||m||ni).If an adversary modifiesC, then this equation will not hold, otherwise this equation will hold.Similarly, if an adversary modifies the message {Auth}, it can be quickly detected because it would not be the same as {Auth′}.In both cases, the authentication would not succeed, and the session would be terminated.Thus, integrity is ensured in the proposed scheme.
6.3.5 Unforgeability
In the proposed IIoT-CS scheme, ifAdtries to produce a legitimate signature, thenAdmust compute the equationS=Xi+(b+Vi).H(IDi||m||ni).For this,Adwould need the private key pair (Vi, Xi) of theith-node.To compute the private keys,Admust solve HECDP which is infeasible.Hence, the proposed IIoT-CS schemes provides security against unforgeability.
6.3.6 Forward Secrecy
In the proposed IIoT-CS scheme, the secret session key is renewed after every session completion process.The secret session key depends on the private valuesb,VjandXjof participating nodes, and it is infeasible for an adversary to find these private values due to HECDLP.Thus,the adversaryAdis not able to read and use the previous messages later.Hence, the proposed scheme ensures forward secrecy.
6.3.7 Security from Replay Attack
An adversary can obtain the previous messages {Wi, Yi}, {Wj, Yj}, {Ti, C, S, Z}, and {Tj,Auth} eavesdropping on the communication channel betweenith-nodeandjth-node.The adversary replays such messages to produce an invalid effect.In the proposed IIoT-CS scheme, the value of C depends on fresh nonce ni, the valueSdepends on the fresh private random numbers b andVi, the value ofZdepends on b, and the value ofAuthdepends on ni and private keyVj.This means that for every session the values ofC,S,Z, andAuthare updated.Therefore, the adversary in the next communication session is incapable to utilize the past messages.Thus, the proposed IIoT-CS scheme ensures security against replay attack.
6.3.8 Security from Eavesdropping Attacks
In the proposed IIoT-CS scheme, the messages are transmitted in plain text, hashed and cipher text format.The plain text messages contain no confidential information and provide no advantage to the adversary.Furthermore, all messages containing confidential information are always protected by using HECDLP, one-way hash function and encryption algorithm, rendering the retrieval of the confidential information computationally infeasible for an adversary.Therefore,the proposed IIoT-CS scheme prevents eavesdropping attacks.
6.3.9 Security from Denial of Service(DoS)Attack
In the proposed IIoT-CS scheme, the participating nodes first check the validity of the received timestamps.If the timestamps are not valid, then the messages are rejected.Furthermore,the information transmitted are complemented by an integrity checks in the form of signature and the encrypted message always contain the latest timestamp.Thus, the proposed scheme can identify incorrect messages and avoid DoS attacks by essentially terminating the session.
6.3.10 Security Against Impersonation Attack
In node impersonation attack, an adversary mimics the behavior of legitimate IoT nodes by eavesdropping on the communication channel.In the proposed IIoT-CS scheme, if theAdmimics the behavior of a valid sender node (ith-node).In doing so,Adproduces a message {Wa,Ya} and sends it to a valid receiver node (jth-node).Thejth-nodereplies the adversary with a message {Wj,Yj}.The adversaryA, when receiving {Wj, Yj}, generate the message {C′,S′,Z′} and send it to thejth-node.As the adversary is incapable to compute the private keys of a valid sender node,the message {C′,S′,Z′} transmitted by the adversary is incorrect.Thejth-node, upon obtaining this inaccurate message {C′,S′,Z′}, decryptC′to validate the signature, but sinceS′.D≠β+ (Z′+Ui).H(IDi||m||ni), thus the authentication fails.Furthermore, the adversaryAdis unable to mimics the behavior of the valid receiver (jth-node) because it is not feasible forAdto compute the private keyVjofjth-node, and thus is unable to correctly produce the message {Auth}, as a result the nodes finish the session.Thus, the proposed scheme ensures security against impersonation attack.
6.3.11 Security from Man in the Middle(Mitm)Attack
In MitM attack, an adversary attempts to modify the messages fromith-nodeto thejthnodeand vice versa.The adversary pretends itself as a valid participating entity and passes the updated messages to either node.The proposed scheme performs the mutual authentication using the messages {C,S,Z} and {Auth}.Adcan only spoof a valid participant if it can produce any of these messages correctly.However, according to HECDLP the retrieval of the private key is computationally not feasible.Thus, the proposed scheme can easily withstand MitM attacks.
6.3.12 Security from Key Compromise Attack
The private keyVjand secret valuebare used to obtain the secret session keySK, the adversary is incapable to get the private values due to HECDLP, as a result the adversary can’t generate the secret session key and hence, the proposed IIoT-CS scheme can ensure security against key compromise attack.
7 Comparative Analysis
This section presents the comparative analysis of computational cost, communication overhead and security features.
7.1 Computational Cost
The computational overhead depends on the execution time of different cryptographic operations involved in an authentication scheme.Garg et al.[23] show that the time required to execute elliptic curve scalar multiplication (ECSM) and hash-to-point (HtP) operations is 0.986 and 14.293 ms, respectively, using MIRACL [39].The execution time of Hyperelliptic Curve Divisor Multiplication (HECDM) is considered as 0.48 ms [40].The time consumption of cryptographic operations is very small compared to the time consumption of ECSM and HECDM and therefore can be ignored.In the proposed scheme, each sender node (ith-node) and the receiver node (jthnode) performs 3 HECDM operations.Therefore, the time consumed by the sender and receiver node together is 6 × 0.48 = 2.88 ms.The KGC performs 3 HECDM operations for at least 2 IoT nodes in the system to authenticate each other.Therefore, the time consumed by the KGC is 3× 0.48 = 1.44 ms.The total time consumed by the KGC and nodes to for mutual authentication is 2.88 ms + 1.44 ms = 4.32 ms.The comparison of the computational cost of IIoT-CS scheme with the existing schemes [15,23,41] is shown in Tab.2 and Fig.4a.It is clear from the results that IIoT-CS scheme is less expensive in computational cost as compared to the existing schemes.

Figure 4:Comparative analysis of (a) computational cost and (b) communication overhead

Table 2:Computational cost analysis
7.2 Communication Overhead
Communication overhead can be determined from the number of bits sent and received by the participating IoT nodes in the authentication phase.We assumed SHA-256 as our hash function, which generates 256-bits output and 128-bit AES as our encryption algorithm which generates 128-bits ciphertext.In the proposed IIoT-CS scheme, an IoT node is required to send two messages {Wi,Yi} and {Ti,C,S,Z} and receive two messages {Wj,Yj} and {Tj,Auth}.The communication overhead of an IoT node to send the message {Wi,Yi} and {Ti,C,S,Z} is 160+ 80 + 80 + 128 + 256 + 80 = 784 bits.Whereas the communication overhead of an IoT node to receive the messages{Wj,Yj} and {Tj,Auth} is 160 + 80 + 80 + 128 = 448 bits.The overall communication overhead of an IoT node is 784 + 448 = 1232 bits.The comparison of the communication overhead of IIoT-CS scheme with the existing schemes [15,23,41] is shown in Tab.3 and Fig.4b.It is clear from the results that IIoT-CS scheme incurs the lowest communication overhead as compared to the existing schemes.
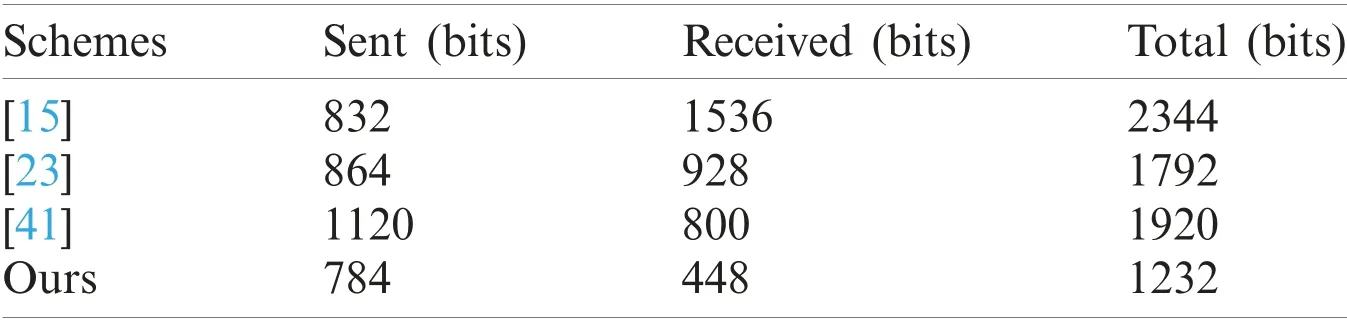
Table 3:Communication overhead analysis
7.3 Comparison of Security Attributes
We compare the proposed scheme’s security functionality with existing state-of-the-art [15,23,41].The proposed scheme offers mutual authentication, non-repudiation, unforgeability, forward secrecy, resist, replay, eavesdropping, DoS, impersonation, MitM, and key compromise attacks as shown in the Tab.4.It is obvious that the proposed IIoT-CS scheme is by far the most secure scheme amongst the existing protocols.

Table 4:Comparison of the security features
8 Conclusion
In this study, we used HEC based CS scheme in the developing of an efficient and secure authentication mechanism for IIoT environment.The proposed scheme uses 80-bit HEC rather than 160-bit ECC for security and performance.We apply both formal and informal security analysis to evaluate the proposed scheme’s security.We performed the formal security analysis by using AVISPA tool and RoR model, which affirms the security of the proposed scheme.It has been shown in the analysis that the proposed scheme offers confidentiality, mutual authentication,integrity, and non-repudiation and is also robust to a range of security attacks such as replay,eavesdropping, impersonation, MitM, DoS, and key compromise attacks etc.Our proposed scheme is relatively less expensive compared to the current state-of-the-art.Our proposed scheme is 31.25% and 51.31% more efficient in computational cost and communication overhead, respectively, compared to the most recent protocol.Thus, our proposed scheme is a viable option for IoT devices with inadequate resources.
9 Future Work
We want to incorporate and evaluate the proposed IIoT-CS scheme in a real-world IIoT environment in the future.This will make more improvements to the proposed scheme and will encourage us to evaluate its security and efficiency more accurately.
Funding Statement:This work is supported by the University of Malaya IIRG Grant (IIRG008A-19IISSN), Ministry of Education FRGS Grant (FP055-2019A).This work was also supported by Grant System of University of Zilina No.1/2020.(Project No.7962) and partially supported by the Slovak Grant Agency for Science (VEGA) under Grant Number 1/0157/21.The authors are grateful to the Taif University Researchers Supporting Project (Number TURSP-2020/36), Taif University, Taif, Saudi Arabia.
Conflicts of Interest:The authors declare that they have no conflicts of interest to report regarding the present study.
杂志排行
Computers Materials&Continua的其它文章
- Hybrid Renewable Energy Resources Management for Optimal Energy Operation in Nano-Grid
- HELP-WSN-A Novel Adaptive Multi-Tier Hybrid Intelligent Framework for QoS Aware WSN-IoT Networks
- Plant Disease Diagnosis and Image Classification Using Deep Learning
- Structure Preserving Algorithm for Fractional Order Mathematical Model of COVID-19
- Cost Estimate and Input Energy of Floor Systems in Low Seismic Regions
- Numerical Analysis of Laterally Loaded Long Piles in Cohesionless Soil
