欺骗攻击下基于集员估计的网络化系统跟踪控制
2022-06-01刘行朱燕飞于家浩
刘行 朱燕飞 于家浩




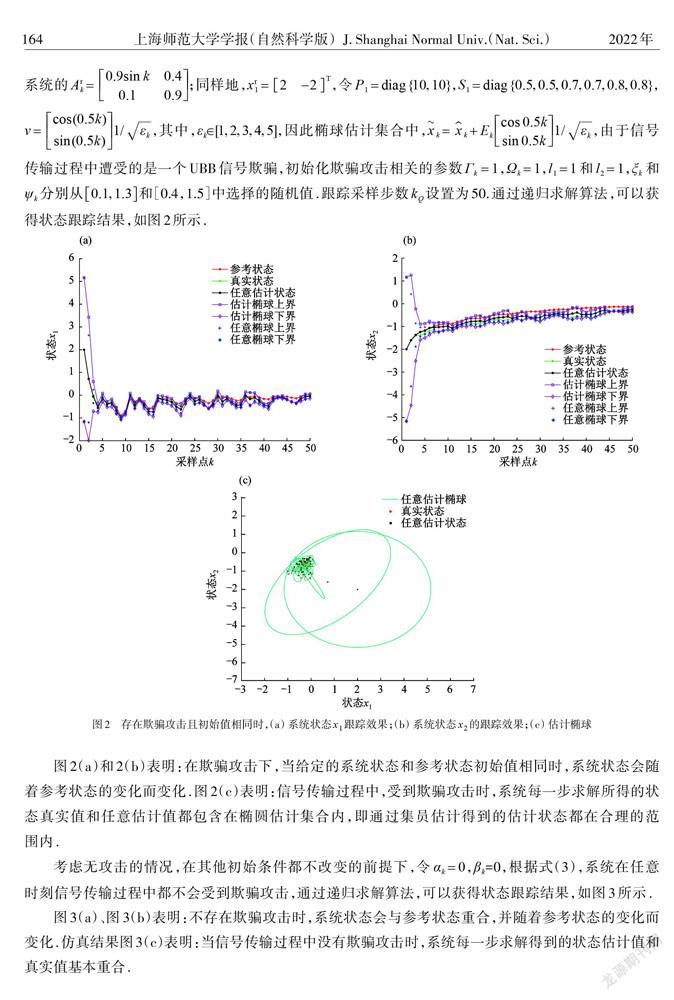

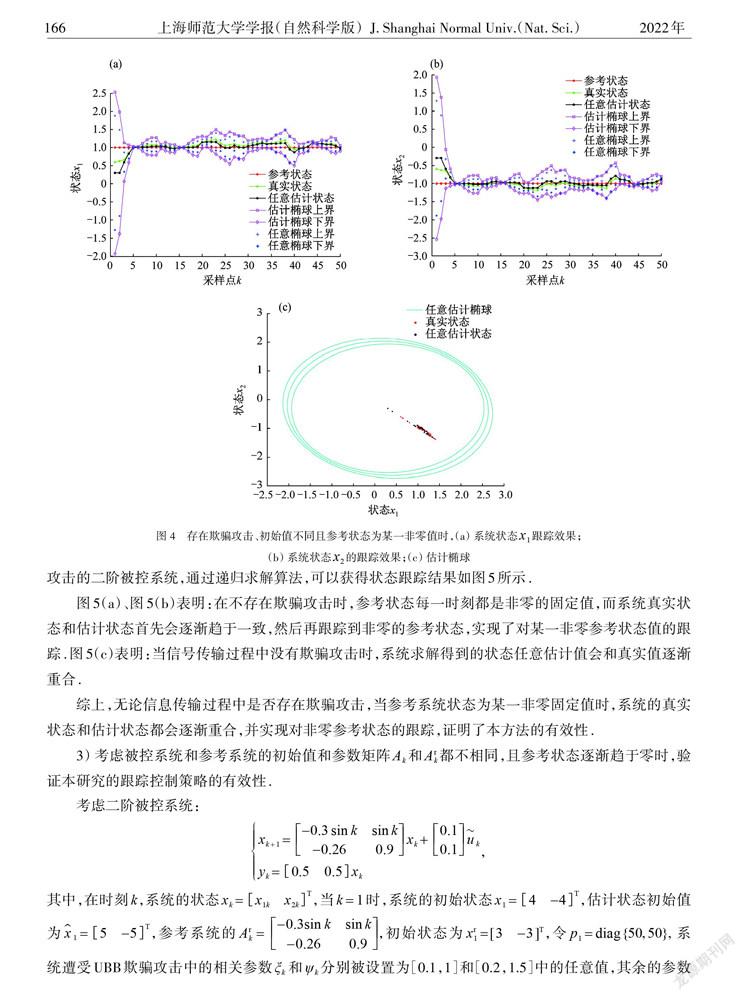
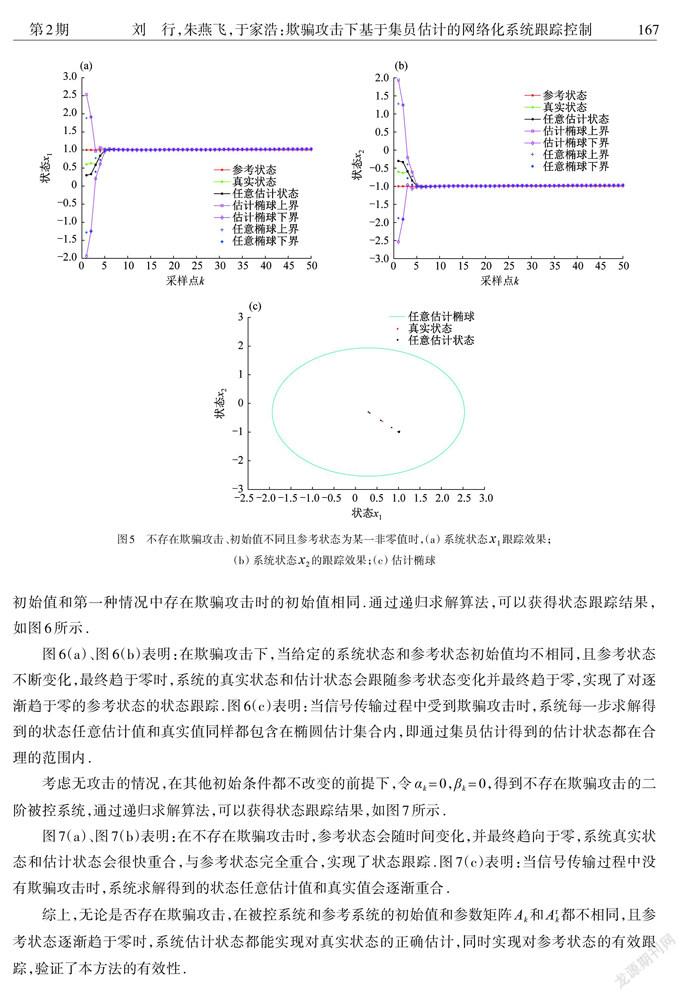
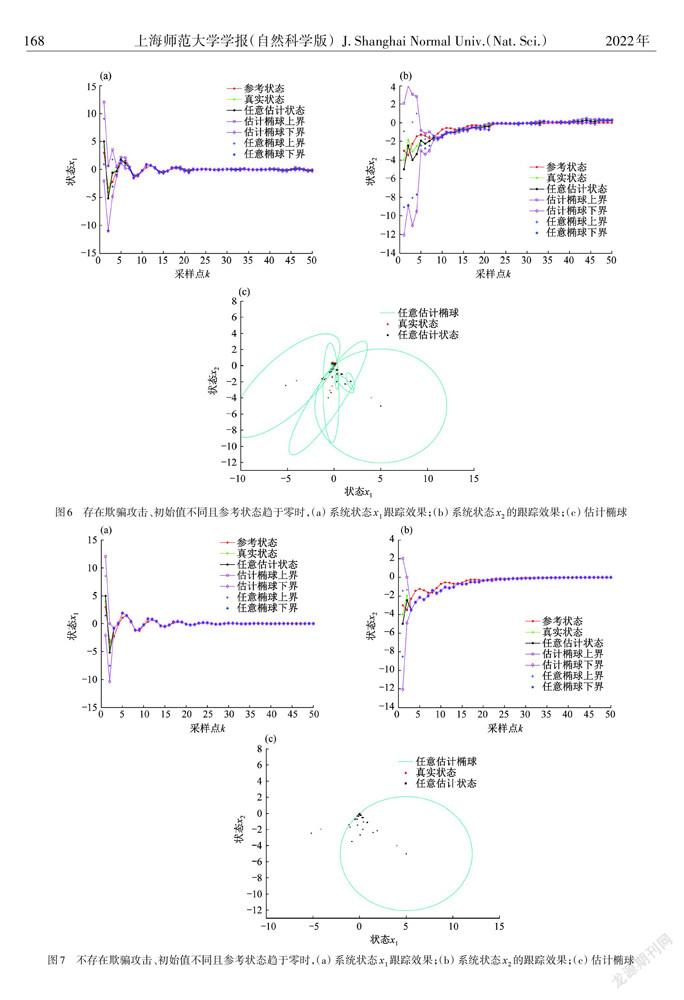




摘 要: 针对在统计特性未知欺骗攻击下,线性时变参数网络化控制系统(NCS)容易出现跟踪偏差的问题,提出了一种基于集员估计的控制策略,实现了系统状态对参考状态的有效跟踪.与卡尔曼估计等方法相比,无需提前知道攻击的统计特性,利用一种新型的集员估计方法,将传感器到控制器通道和控制器到执行器通道遭受的欺骗攻击建模为未知但有界(UBB)的信号,其中系统真实状态和估计状态都存在于估计集中.该方法提高了估计的准确性,并扩大了适用范围.采用Lyapunov函数,给出了误差闭环系统稳定的充分条件和基于线性矩阵不等式的估计器和控制器的求解算法,并使用凸优化方法获得最佳的估计集.用数值仿真验证所提出方法的可行性.
关键词: 网络化控制系统(NCS); 集员估计; 跟踪控制; 欺骗攻击
中图分类号: TP 273; TN 911.7 文献标志码: A 文章编号: 1000-5137(2022)02-0157-14
LIU Hang, ZHU YanfeiYU Jiahao
(College of Information, Mechanical and Electrical Engineering, Shanghai Normal University, Shanghai 201418, China)
Considering the tracking deviation of the linear variable parameter networked control system(NCS) under a deception attack with unknown statistical characteristics, a novel control strategy based on set-membership estimation was proposed to realize the effective tracking of the system state to the reference system state. Firstly, compared to methods such as the Kalman estimation with the known statistical characteristics of the attack in advance, a novel set-membership estimation was proposed to improve the accuracy and application scope of the estimation, in which the deception attack suffered in the sensor-to-controller channel and the controller-to-actuator channel only needed to be modeled as an unknown but bounded(UBB) signal, and to guarantee that the true state and estimated state of the system consisted in the estimated set. Secondly, the sufficient conditions for the stability of the error closed-loop system based on the Lyapunov function were given. Simultaneously, the solving algorithm of the estimator and the controller based on the linear matrix inequality was obtained, and the convex optimization method was adopted to achieve the best estimation set. Finally, the feasibility of the proposed method was verified by numerical simulation.
networked control system(NCS); set-membership estimation; tracking control; deception attacks
0 引 言
随着互联网以及无线通信的飛速发展,物理设备之间的通信距离不再局限于本地,先进的通信网络可以为分布于不同地点的两台或多台物理设备,提供快速可靠的通信方案.在此背景下,网络化控制系统(NCS)应运而生,并在近几年广泛应用于交通、电力以及机器人远程控制系统等领域.跟踪控制作为NCS的一个研究方向,受到越来越多的人关注,其主要目标是保证被控对象的状态可以较好地跟踪参考状态,在无人机及机器人轨迹跟踪控制等方面应用广泛.但是基于公共网络的通信方式也给跟踪控制带了一些挑战,例如,网络带宽的有限性和不可避免的网络拥塞通常会引起一些网络诱导时延、数据丢包等问题,进而影响NCS的跟踪效果.除此之外,一些人为的恶意攻击也会破坏NCS传输数据的完整性和准确性,一定程度上来说,刻意的网络攻击是一种更为严重的破坏.因此,采取有效的措施,避免恶意的网络攻击以及保证NCS在被攻击后的快速恢复能力至关重要.
目前的大多数研究把常见的网络攻击分为3大类:拒绝服务(DoS)攻击、重放(reply)攻击及欺骗(deception)攻击.对于DoS攻击,攻击者会阻塞通信信道,最终导致带宽资源被耗尽;对于reply攻击,攻击者会不断重发之前已经发送过的数据,导致控制器不能实时接收到当前时刻的消息;欺骗攻击和前两种攻击不同,攻击者会在传输的真实数据中注入虚假数据,伪装成真实数据,因此欺骗攻击是一种更隐蔽、破坏性更强的攻击.目前,只有少部分文献考虑了网络攻击下的跟踪控制问题,如TANG 等考虑存在DoS攻击的情况下,制定一种事件触发条件,保证移动机器人的跟踪收敛以及网络资源的有效利用;JIANG等研究了一类存在故障和DoS攻击下,不确定系统的分散自适应模糊跟踪控制问题;FENG 等研究了基于随机马尔可夫过程的多智能体系统的分布式安全一致性跟踪控制问题,通过建立一种混合随机安全控制框架,实现了均方指数一致性跟踪;WAN等在异步攻击场景下,设计了一种选择反馈增益矩阵和耦合强度的算法,以确保能够实现异构网络系统的一致性跟踪.目前研究主要集中使用伯努利随机过程等模型,描述攻击或使用卡尔曼滤波进行状态估计,以上方法都需要提前假设攻击的先验知识,如概率分布、期望等,而在实际问题中,攻击的先验知识很难准确被获取.因此,建立合适的网络攻击模型是保证实现准确跟踪的重要基础.未知但有界(UBB)信号模型是一种只要求信号有界,并对信号统计特性没有限制的模型,经常用来描述过程和测量噪声.事实上,一些欺骗攻击也是能量有界的,它不会持续攻击传输信号,每次攻击幅度也不会无限大,因此本文作者使用UBB信号描述欺骗攻击,与需要预知攻击先验知识的模型相比,所研究的模型具有更加广泛的适用范围.
另外,UBB信号经常在集员估计中被用于提高集员估计的估计精度.集员估计是近几年被大家广泛讨论的热点话题,其估计结果不是单个估计点,而是包含系统真实状态的估计集合,集合中的任意值都可以作为在合理范围内系统真实状态的估计值,与一些点估计方法相比(例如卡尔曼估计),这种灵活的估计方法大大降低了对传感器测量精度的要求.集员估计作为一种切实可行的估计方法,已经应用在各个领域中,ZHOU等使用扩展非线性集员滤波器对多传感器数据进行融合,实现室内移动机器人的长距离实时定位;MOUSAVINEJAD等通过计算集员估计集是否存在交并集,判断NCS中是否存在网络攻击;TANG等提出了一种基于未知输入的集员估计器,对执行器故障进行诊断.目前把集员估计使用在NCS跟踪控制问题上的研究较少,MOUSAVINEJAD 等提出了一种弹性集员估计策略,保护系统不受网络攻击,并保证系统状态和参考状态都包含在估计集合内,从而实现状态跟踪.除此之外,在跟踪控制问题上,很少有人利用集员估计集为跟踪控制提供可靠的估计状态.在实际应用中,当估计的状态从估计器传到控制器时,往往会出现传输错误,如果使用估计集合中特定点作为控制率,将很难保证估计点的有效性.
基于以上研究现状,本文作者使用UBB信号模型、集员估计理论和Lyapunov稳定性理论,研究欺骗攻击下NCS的跟踪控制问题,找到保证集员估计有效性的充分条件.在此基础上,建立误差闭环系统,分析闭环系统的稳定性,从而确保所考虑的系统状态对参考状态的有效跟踪.主要工作如下:
设计了一种基于集员估计的跟踪控制策略,估计状态使用集员估计集中的任意值而不是特定的估计点,同时系统的真实状态和任意估计状态都包含在集员估计集中,保证了估计点的有效性.
建立误差闭环系统,把在受到UBB信号欺骗攻击下,系统的状态跟踪问题转化为闭环系统的有限时間—集员估计输入到状态稳定性(FT-smISS)问题,保证系统跟踪的有效性.
1 问题描述及初步准备
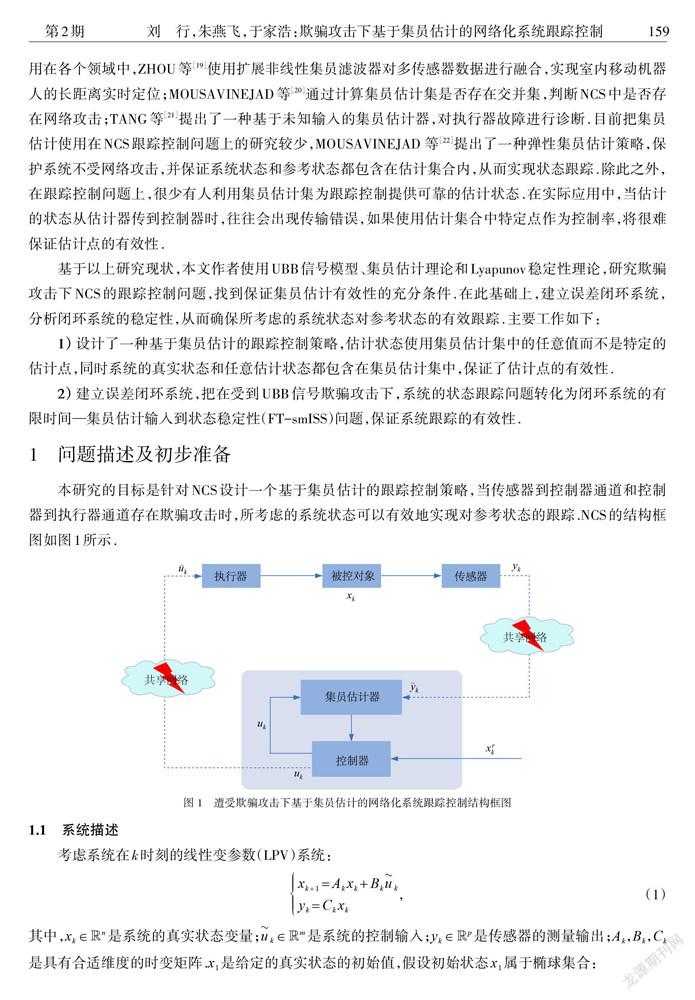
本研究的目标是针对NCS设计一个基于集员估计的跟踪控制策略,当传感器到控制器通道和控制器到执行器通道存在欺骗攻击时,所考虑的系统状态可以有效地实现对参考状态的跟踪.NCS的结构框图如图1所示.
系统描述
基于集员估计的跟踪控制协议
集员估计跟踪控制问题
4 结 论
考虑了在UBB欺骗攻击下线性时变参数的NCS,设计了一种基于集员估计的控制策略,使用估计集中的任意值代替某一特定值作为跟踪控制策略中的估计状态,提高了估计的有效性.构造了一个误差闭环系统,将被控系统的状态跟踪问题转化为误差闭环系统的稳定性问题,提出了保证集员估计可用性和状态跟踪有效性的充分条件.最后讨论了3种情况下系统的跟踪效果,验证了所提方法的可行性.
参考文献:
[1] LI S B, WANG Z, ZHANG W D, et al. Status and prospect of networked control system [J]. Information and Control, 2003,32(3):239-244.
[2] BAI T, WU Z M, YANG G K. Networked control systems(NCSs) [J]. Control Theory & Applications,2004,21(4):584-590.
[3] JIANG L B, HONG S. Research on the application of intelligent vehicle path tracking control [J]. Machine Design and Manufacturing Engineering,2021,50(6):51-55.
[4] ZHANG S J, LI S, YAN P, et al. Switching LPV robust tracking control for helicopters [J]. Journal of Nanjing University of Aeronautics & Astronautics,2021,53(2):260-266.
[5] ; WANG K Y, WEI L N, TIAN E G, et al. Memory?event⁃triggered control of networked control systems subject to DoS attacks [J]. Information and Control,2019,48(5):528-535.
[6] HUANG L, GUO J, ZHANG H Y. Observer⁃based dynamic event triggering control for networked systems with periodic denial⁃of⁃service attack [J]. Control Theory & Applications,2021,38(6):851-861.
[7] FRANZ G, TEDESCO F, FAMULARO D. Resilience against replay attacks: a distributed model predictive control scheme for networked multi⁃agent systems [J]. IEEE/CAA Journal of Automatica Sinica,2021,8(3):628-640.
[8] YANG J J, ZHANG Z D, XIE L B. Coding detection scheme for replay attack based on the control performance index [J]. Information and Control,2021,50(3):329-336.
[9] DING D R, WANG Z D, HO D W C,et al. Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks [J]. Automatica,2017,78:231-240.
[10] LI F Q, GAO L S, ZHENG B Z, et al. Event⁃triggered secure control for networked systems under deception attacks [J]. Computer Engineering and Applications,2021,57(5):264-270.
[11] TANG Y, ZHANG D, HO D W C, et al. Event⁃based tracking control of mobile robot with denial⁃of⁃service attacks [J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems,2018,50(9):3300-3310.
[12] JIANG X, MU X, HU Z. Decentralized adaptive fuzzy tracking control for a class of nonlinear uncertain interconnected systems with multiple faults and denial⁃of⁃service attack [J]. IEEE Transactions on Fuzzy Systems,2021,29(10):3130-3141.
[13] FENG Z, WEN G, HU G. Distributed secure coordinated control for multiagent systems under strategic attacks [J]. IEEE Transactions on Cybernetics,2017,47(5):1273-1284.
[14] WAN Y, CAO J D. Observer⁃based tracking control for heterogeneous dynamical systems under asynchronous attacks[C]// 2017 International Workshop on Complex Systems and Networks (WCSN). Doha: IEEE,2017:224-229.
[15] DING D R, SHEN Y X, SONG Y, et al. Recursive state estimation for discrete time?varying stochastic nonlinear systems with randomly occurring deception attacks [J]. International Journal of Genaral Systems,2016,45(5):548-560.
[16] WEI G L, LIU S, WANG L C, et al. Event⁃based distributed set⁃membership filtering for a class of timevarying non-linear systems over sensor networks with saturation effects [J]. International Journal of General Systems,2016,45(5):532-547.
[17] WENG P D, CHEN B, YU L. Fusion estimate of FDI attack signals [J]. Acta Automatica Sinica,2021,47(9):2292-2300.
[18] ZHANG Y L, ZHU Y F, FAN Q Q. A novel set⁃membership estimation approach for preserving security in networked control systems under deception attacks [J]. Neurocomputing,2020,400(4):440-449.
[19] ZHOU B, QIAN K, MA X D, et al. Multi⁃sensor fusion for mobile robot indoor localization based on a set⁃membership estimator [J]. Control Theory & Applications,2017,34(4):541-550.
[20] MOUSAVINEJAD E, YANG F, HAN Q L, et al. A novel cyber attack detection method in networked control systems [J]. IEEE Transactions on Cybernetics,2018,48(11):3254-3264.
[21] TANG W T, WANG Z H, WANG Y, et al. Fault diagnosis for uncertain systems based on unknown input set-membership filters [J]. Acta Automatica Sinica,2018,44(9):1717-1724.
[22] MOUSAVINEJAD E, GE X, HAN Q L, et al. Resilient tracking control of networked control systems under cyber attacks[J]. IEEE Transactions on Cybernetics,2021,51(4):2107-2119.
(责任编辑:包震宇,冯珍珍)
