Intelligent Tunicate Swarm-Optimization-Algorithm-Based Lightweight Security Mechanism in Internet of Health Things
2021-12-14GiaNhuNguyenNinHoLeVietGyanendraPrasadJoshiandBhanuShrestha
Gia Nhu Nguyen,Nin Ho Le Viet,Gyanendra Prasad Joshi and Bhanu Shrestha
1Faculty of Information Technology,Duy Tan University,Da Nang,550000,Vietnam
2Graduate School,Duy Tan University,Da Nang,550000,Vietnam
3Department of Computer Science and Engineering,Sejong University,Seoul,05006,South Korea
4Department of Electronic Engineering,Kwangwoon University,Seoul,01897,South Korea
Abstract:Fog computing in the Internet of Health Things(IoHT)is promising owing to the increasing need for energy-and latency-optimized health sector provisioning.Additionally,clinical data(particularly,medical image data)are a delicate,highly protected resource that should be utilized in an effective and responsible manner to fulfil consumer needs.Herein,we propose an energy-efficient fog-based IoHT with a tunicate swarm-optimization-(TSO)-based lightweight Simon cipher to enhance the energy efficiency at the fog layer and the security of data stored at the cloud server.The proposed Simon cipher uses the TSO algorithm to select the optimal keys that will minimize the deterioration of quality between the original and reconstructed(decrypted)images.In this study,the decrypted image quality is preserved by the peak signal-to-noise ratio(PSNR)such that consumers can generate precise medical reports from IoHT devices at the application level.Moreover,a lightweight encryption step is implemented in the fog to improve energy efficiency and reduce additional computations at the cloud server.Experimental results indicate that the TSO-Simon model achieved a high PSNR of 61.37 dB and a pixel change rate of 95.31.
Keywords:Internet of Health Things;healthcare;Simon cipher;tunicate swarm optimization
1 Introduction
The Internet of Things(IoT)provides different apparatuses and assets to build an incorporated healthcare framework for better treatment,cost-effective medical services,and positive treatment results[1].The healthcare field,which is slow in embracing new advances,is expected to develop rapidly and will involve more than 50 million associated devices.Additionally,extraordinary application areas in health-related services have demonstrated different prospects of IoT application;according to the present pattern,smart healthcare services in the application space(e.g.,smart pills,smart dispensing gadgets and syringes,smart observing gadgets,smart radio-frequency identification(RFID)cabinets,and electronic health records)are the latest development[2].The Internet of Health Things(IoHT)pertains to the exchange of data and processing of information to screen a patient’s health status[3].Numerous healthrelated institutions are now utilizing the IoHT for various purposes from monitoring infants to tracking inventory and resources.Two classes of operation cases exist:one for clinical administration and the other for support activities.In clinical settings,the IoHT enhances patient-centric exercises through remote patient monitoring.This pertains to clinical preliminaries,where the IoHT actively tracks important signs and other indicators essential to the examination,e.g.,glucose levels and weight patterns.The IoHT facilitates support tasks by enabling the improved usage of portable clinical resources,which will reduce overall operational expenses[4].Executing processes on the cloud may result in latencies that are inappropriate for certain application spaces,causing significant difficulties in providing real-time and conventional cloud computing(CC)[5].CC provides a complete package,which benefits the clients;however,it has certain disadvantages.One of the advantages of the IoT is its rapid processing and computing of big data,which are generated and managed effectively in different applications.Smart healthcare frameworks are required,particularly to manage the rapidly changing pace of human life.Introducing fog computing and the IoT in machines relevant to clinical industry applications enables the productivity of tasks to be improved in such healthcare frameworks[6].
Fog computing enables on-time service delivery with consistency while addressing the problems related to CC,e.g.,cost overheads,delays,and jitters while transferring data to the cloud.In addition,it involves a distributed design that enhances the computational capacity and networking assets in CC.It provides speedy access to assets,e.g.,computing and storage for healthcare applications[7].Furthermore,two fundamental concerns arise when transferring information to the cloud:(1)security and(2)access control.Therefore,information protection and access control should be guaranteed for approved clients of cloud-supported IoT.The conventional method for safeguarding private information is encryption;however,encryption schemes do not provide access control[8].Moreover,it is difficult to structure a proficient security upgrading system that protects against unapproved access to the client’s personal health information while simultaneously releasing an adequate amount of data to the cloud-based healthcare-related recommender administration to extract helpful suggestions[9].Meanwhile,a secure IoT framework for in-home healthcare applications,including elderly patient information(e.g.,big data,typically up to 23 GB/person/week generated from patient homes),should be established to guarantee information privacy and reliability,regardless of whether the information transfer speeds are affected by the security overhead of the communication protocols[10].
Herein,we propose an energy-efficient and minimal-delay fog based on the IoHTwith a tunicate-swarmoptimization-(TSO)-based lightweight Simon cipher to enhance the cloud data security.In this section,we introduced some of the fog-based IoHT advantages and applications as well as the disadvantages of the cloud layer.
The remainder of this paper is organized as follows.Section 2 presents a review of relevant studies.Section 3 provides a detailed explanation of the proposed IoHT data security model.Section 4 presents the results of an experiment performed to prove the efficiency of the proposed method.Section 5 concludes the paper.
2 Literature Review
Mukherjee et al.[11]proposed a framework wherein the weighted majority game hypothesis was utilized to select fog gadgets in indoor and outdoor areas.The health information gathered using a body area network was stored and managed inside cloud servers.Clients could access their health information using their cell phones while simultaneously obtaining healthcare counsel.To decrease the energy utilization and delay over remote cloud servers,fog computing was used.
Mutlag et al.[12]presented a survey regarding innovations in fog computing in the healthcare IoT framework.Fog computing with no interruptions decreases latency compared with CC and is beneficial to healthcare-related IoT frameworks owing to its real-time prerequisites.
Santos et al.[13]conducted a review that introduced the advances of the most recent investigations based on clinical considerations and an assisted environment.They focused on articles pertaining to online observation,diagnosis,and support for the identification of cardiovascular ailments.They introduced a reference model based on the assessment of assets obtained from selected examinations.Further,their proposed method can assist future enthusiasts in discovering and specifying the necessary elements to establish a model for online heart monitoring purposes.Stergiou et al.[14]proposed a method for incorporating CC into the IoT as a fundamental state for big data.In addition,they attempted to build a structure that relies on the security of the system to enhance data security.Moreover,they proposed a solution by introducing a security “wall” between the cloud server and the Internet to eliminate confidentiality and security issues.
Manikandan et al.[15]proposed an IoT-based scheduling technique,called the hash polynomial twofactor decision tree(HP-TDT),to increase scheduling efficiency and reduce response time by categorizing patients as being normal or in a critical state within a short time.The HP-TDT planning strategy included three phases:the registration,data sorting,and scheduling stages.The registration step was performed using the open address hashing model to reduce the key generation response time.Subsequently,the data assortment stage was performed using the polynomial data collection algorithm.
3 Proposed Model
The IoHT has become a challenging application of the IoT and CC,where the exchange and processing of health information are performed to observe the health status of patients.The health-related information collected is stored and managed inside cloud servers.Users can obtain their health data using their cell phones and can obtain healthcare advice simultaneously.Medical information is a sensitive,highly protected asset that should be prepared in an effective and trustworthy manner.Moreover,sensitive personal information is subject to privacy leakage owing to unapproved access,accidental loss,or resale of IoHT devices.The structure of the proposed energy-efficient fog-based cloud IoHT security model is illustrated in Fig.1.
In this study,we developed a high-security data storage approach using a Simon cipher-based encryption method to secure medical image data with less complexity in cloud servers.Moreover,to improve the efficiency of the encryption method,we included the optimal key selection method based on the TSO algorithm to improve the visual quality of the decrypted images.Healthcare systems using fog computing are emerging because of the increasing need for energy- and latency-optimized health service provisioning.Hence,to enhance reliability and reduce energy consumption over remote cloud servers,a data security scheme was implemented in a fog layer that was closer to the cloud layer.The proposed IoHT data security model encrypts data by obtaining the optimal key for which the quality of the decrypted image is similar to that of the original secret image.This is because medical image data are extremely sensitive and a slight change in them can result in incorrect medical report generation.Therefore,the quality of medical images must be prioritized when securing the images.Hence,the proposed data security model was designed to obtain the optimal key with the peak signal-to-noise ratio(PSNR)(i.e.,the indicator used to determine the image quality)value of the decrypted image.
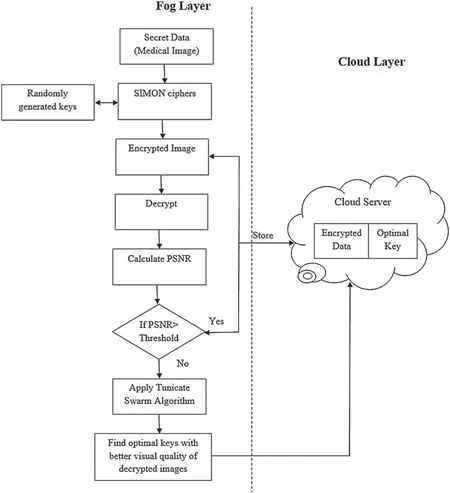
Figure 1:Structure of the proposed model
3.1 Design of IoHT Framework
The structural plan of an IoHT system should ensure an undisrupted data stream for precise and ideal dynamic decision making.The IoHT system in this study was designed to have five layers,i.e.,the perception,mist,fog,cloud,and application layers.Each layer was designed using predefined functionalities applicable to the IoHT system’s information transmission and processing pipeline[16–20].
●Perception layer:The perception layer is responsible for identifying physical objects and assembling appropriate healthcare information from gadgets including real-time and non-real-time information.
●Mist layer:The mist computing layer optimizes time-consuming data processing(i.e.,through data preprocessing strategies)and contributes to ideal resource utilization.
●Fog layer:The fog layer can be used to process data “on the y” to recognize anomalies,provide warning alarms in real time,and initiate important activities automatically.This demands a framework with high responsiveness and negligible latency,thereby limiting the load on the cloud.
●Cloud layer:The entire healthcare information from the fog layer is sent to the cloud layer for longterm storage and finer examination.
●Application layer:The uppermost application layer provides user interfaces between IoHT consumers and the system itself to directly access the produced healthcare status.
In the proposed IoHT data security model,medical image data are collected from the perception layer and secured at the fog layer to reduce the amount of computation required to secure the data at the cloud.For securing data,lightweight Simon block ciphers are used to enhance the energy efficiency of the fog layer.Next,the data are stored on cloud servers and sent to the application layer for user interfaces.Thus,cloud memory and time can be conserved.
3.2 Fog-Based IoHT Data Security Using Simon Ciphers
In this section,the proposed optimal and energy-efficient fog-based IoHT data security model using Simon ciphers is discussed.Simon ciphers are lightweight block ciphers that are primarily intended for resource-control strategies.However,because of the service necessities of large-scale IoHT systems,the requirement for proficient software implementation usage cannot be precluded.Therefore,we introduced TSO-based Simon ciphers in the proposed energy-efficient fog-based IoHT model to enhance the security level in the cloud platform.In the proposed TSO-based Simon ciphers,an optimal key is selected for the encryption of medical images.The proposed security model encrypts the clinical image data at the fog layer and stores the encrypted data along with its key in the cloud server.This enhances the data security and reduces the amount of computation required in the cloud server to safeguard the data from intruders[21–29].
3.2.1 Simon Ciphers
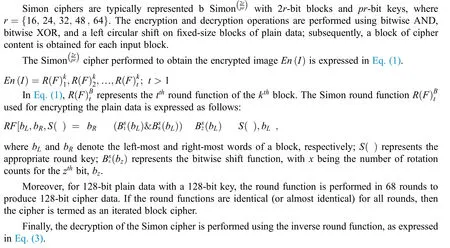
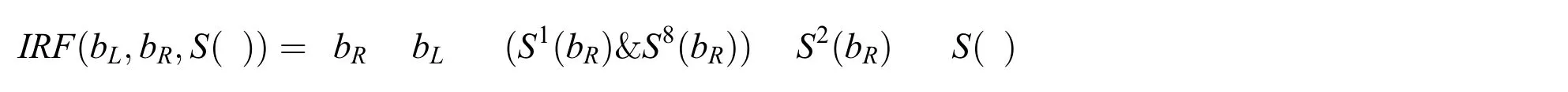
In the proposed Simon cipher,the keys are optimized using the TSO algorithm,i.e.,they are selected for improving the decrypted image quality.
3.2.2 Key Optimization by TSO Algorithm
The TSO algorithm was developed by imitating the jet propulsion and swarm intelligence behaviors of tunicates in obtaining food sources,i.e.,their optimum behaviors[30].Hence,a tunicate must fulfil three criteria:avoid con icts between search agents,move toward the position of the best search agent,and remain near the best search agent to model the jet propulsion behavior mathematically while the swarm behavior updates the positions of other search agents based on the best optimal solution.
By implementing TSO,we optimized the keys used for encrypting private medical images.Typically,optimization methods are implemented using an objective function(also known as the fitness function);toward that fitness value,the optimization problem is converged to produce the optimal solution.In this study,the objective function is the minimization function of the PSNR value calculated between the decrypted image and the original plain images.During every iteration,the PSNR value is verified,and the best keys that can maintain the decrypted image quality are selected.Therefore,the proposed Simon cipher can encrypt images without deteriorating the decrypted image quality as well as minimize the computation time required for the encryption.The steps involved in the proposed TSO algorithm are presented in the following section.
Step 1:Initialization
During initialization,the population(Nmk,wherem=1,2,…,candk=1,2,…,a)of tunicates(i.e.,set of key values)is determined randomly.
Step 2:Fitness Evaluation
Once the initial set of key values is generated,the fitness of the input solutions is assessed,and then the best one is selected during the fitness evaluation step.The fitness function can be defined as
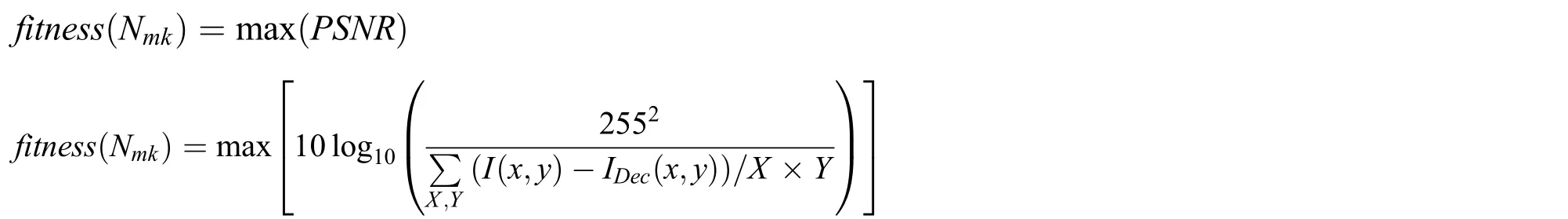
whereI(x,y)andIDec(x,y)represent the plain and decrypted images,respectively;(x,y)represents the row and column of the image.IfPSNRThreshold,the current solutions are saved,and the algorithm further attempts to improve or maintain the maximal fitness value.
Step 3:Avoiding con icts between search agents
The new search agent position(i.e.,newer keys)is calculated using a vectorto avoid con icts between search agents(i.e.,other tunicates)based on the following equation:



4 Results and Discussion
The results provided in this section were acquired from the proposed IoHT data security model implemented on a PC with the following parameters:CPU Intel®Pentium 1.9 GHz,64-bit operating system,Microsoft®Windows 10,and 4 GB of RAM;furthermore,MathWorks MATLAB R2014b was used.All experiments were performed for a set of medical image data,of which a few examples are shown in Fig.2.
Moreover,the encrypted and decrypted image results obtained for the proposed Simon-based IoHT data security model in the fog layer are provided in Tab.1.

Figure 2:Medical images used in this study
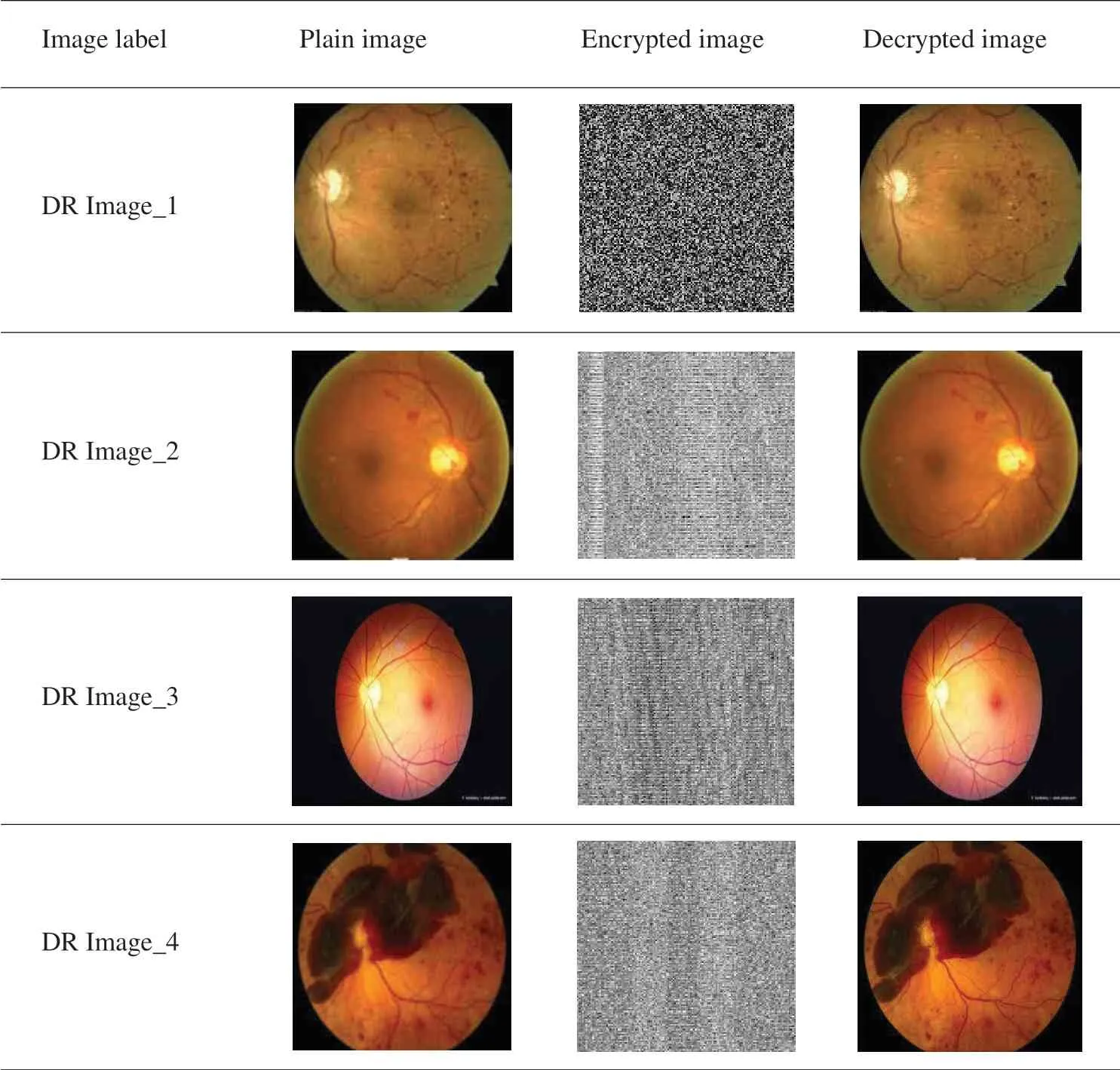
Table 1:Experimental results of the proposed model
4.1 Performance Analysis
To evaluate the performance of the proposed IoHT image data security model,certain indicators such as the number of pixel changing rate(NPCR)and PSNR were considered to determine the encrypted image quality.The NPCR is designed to test the number of changing pixels and the number of average changed intensities between encrypted images.During encryption,the NPCR pertains primarily to the absolute number of pixels that change in value,which can be written as

Moreover,the PSNR representing the maximum possible power of the signal and the power of corrupted noise affecting the fidelity can be written as
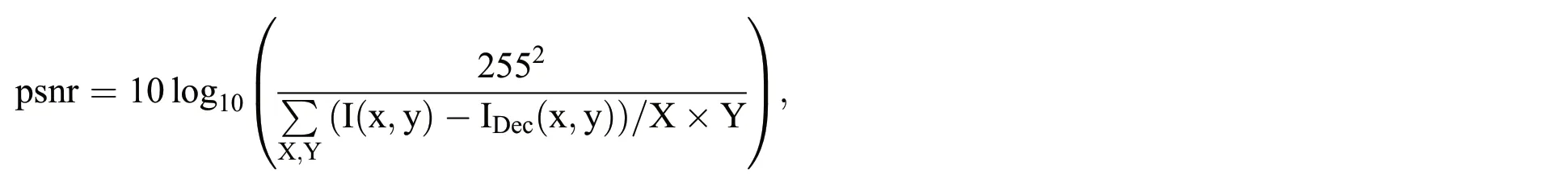
where I (x,y)and IDec(x,y)represent the plain and decrypted images,respectively,with (x,y)pixel locations.
4.2 Results Analysis
The results of encryption using the proposed TSO-based Simon(TSO_Simon),opposition-based particle swarm optimization with Simon(OPSO_Simon),and traditional Simon for a set of diabetic retinopathy(DR)images are shown in Tab.1.A comparison of the results was performed based on the PSNR and NPCR.
Tab.2 provides a detailed comparative analysis of the proposed model in terms of the PSNR and NPCR.The values listed in the table indicate that the proposed TSO_Simon model performed the best among the three methods.For DR Image_1,the TSO_Simon model achieved a maximum PSNR of 61.58 dB,whereas the OPSO_Simon and Simon models obtained minimum PSNR values of 54.52 and 45.92 dB,respectively.Similarly,for DR Image_2,the TSO_Simon model yielded a high PSNR of 63.21 dB,whereas the OPSO_Simon and Simon models yielded lower PSNR values of 56.15 and 47.81 dB,respectively.Likewise,on DR Image_3,the TSO_Simon model achieved a maximum PSNR of 60.74 dB,whereas the OPSO_Simon and Simon models obtained minimum PSNR values of 51.86 and 52.72 dB,respectively.Moreover,for DR Image_4,the TSO_Simon model achieved a high PSNR of 59.95 dB,whereas the OPSO_Simon and Simon models obtained lower PSNR values of 53.32 and 51.24 dB,respectively.
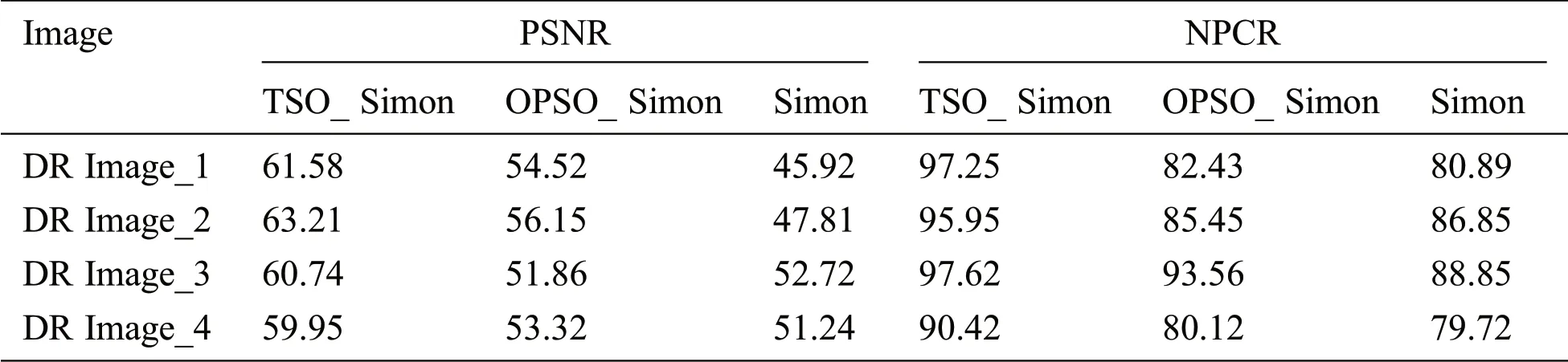
Table 2:Comparative analysis
Additionally,the proposed TSO_Simon model was assessed based on the NPCR.On DR Image_1,the TSO_Simon model achieved a maximum NPCR of 97.25,whereas the OPSO_Simon and Simon models obtained minimum NPCR values of 82.43 and 80.89,respectively.Similarly,on DR Image_2,the TSO_Simon model achieved a high NPCR of 95.95,whereas the OPSO_Simon and Simon models obtained lower NPCR values of 85.45 and 86.85,respectively.Likewise,on DR Image_3,the TSO_Simon model achieved a high NPCR of 97.62,whereas the OPSO_Simon and Simon models obtained lower NPCR values of 93.56 and 88.85,respectively.Moreover,on DR Image_4,the TSO_Simon model achieved a high NPCR of 90.42,whereas the OPSO_Simon and Simon models obtained lower NPCR values of 80.12 and 79.72,respectively.
Tab.2 shows that the maximum PSNR of 63.21 was achieved for DR Image_2 using the proposed method,whereas it is lower for other existing methods.Likewise,the PSNR values of the other DR images were compared with those of existing methods.The obtained values show that the proposed TSObased Simon method improved the image quality significantly compared to the other methods.In addition,the NPCRs of the proposed and existing methods were compared for the DR images.DR Image_1 and DR Image_3 yielded NPCR values greater than 97 using the proposed method,whereas the values were lower for existing methods.This demonstrates the better security attained while encrypting the medical image samples.It is clear from Tab.2 that the proposed TSO_Simon outperformed the other existing methods.
Finally,graphical representations of the results obtained using the proposed and other Simon-based encryption techniques are shown in Figs.3 and 4 to clearly depict the changes in values among the methods compared.
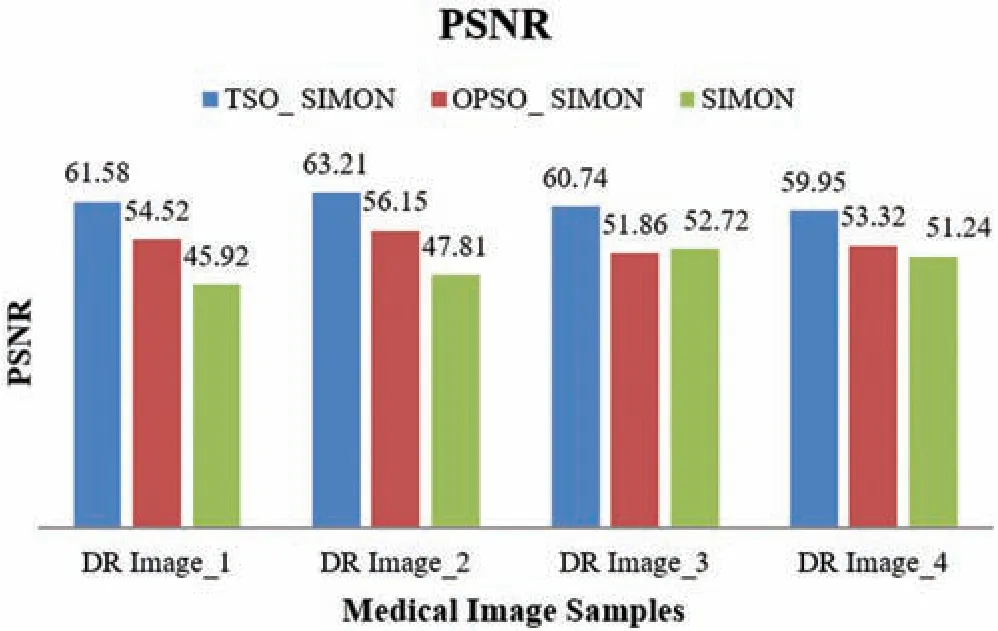
Figure 3:PSNR comparison among different Simon-based encryption techniques
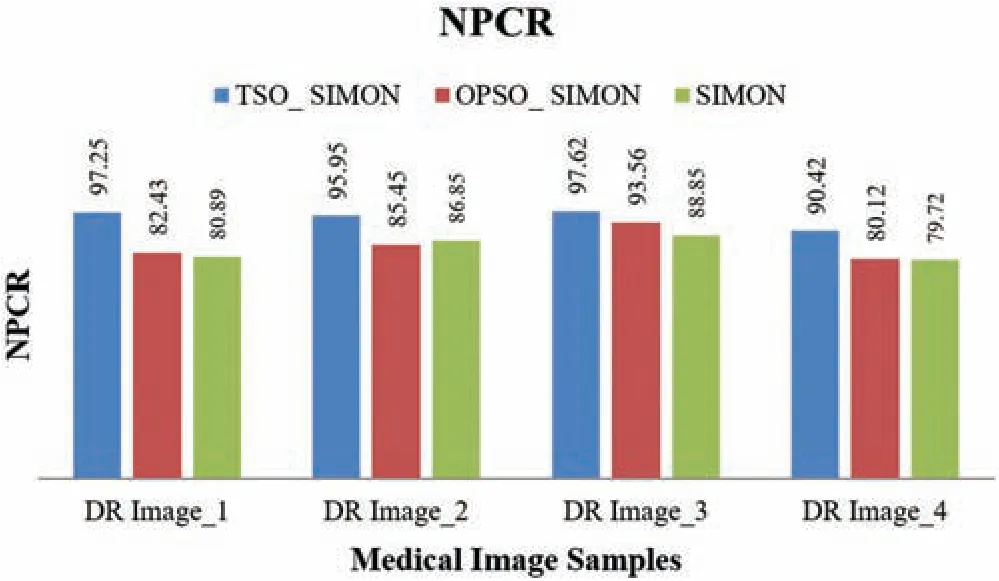
Figure 4:NPCR comparison among different Simon-based encryption techniques
5 Conclusion
In this study,we developed an energy-efficient fog-based IoHT data security model to secure medical image data in a cloud server.The various layers of the IoHT structure were discussed herein.The TSObased Simon encryption method was implemented in the fog layer to improve the energy efficiency,and encrypted private medical data were stored in the cloud.The performance of the proposed IoHT data security model was analyzed based on its PSNR and NPCR and compared with those of other Simon-based encryption methods.The results showed that the highest PSNR value of 63.21 was achieved using the proposed TSO_Simon method,whereas the value was low for the existing methods.In the future,the mist layer of the IoHT architecture will be implemented with optimal resource allocation using advanced optimization methods.
Funding Statement:The authors received no specific funding for this study.
Conflicts of Interest:The authors declare that they have no con icts of interest to report regarding the present study.
杂志排行
Computers Materials&Continua的其它文章
- Design of Authoring Tool for Static and Dynamic Projection Mapping
- Detecting Lumbar Implant and Diagnosing Scoliosis from Vietnamese X-Ray Imaging Using the Pre-Trained API Models and Transfer Learning
- Design of a Compact Monopole Antenna for UWB Applications
- A Smart Wellness Service Platform and Its Practical Implementation
- Fingerprint-Based Millimeter-Wave Beam Selection for Interference Mitigation in Beamspace Multi-User MIMO Communications
- Multilayer Self-Defense System to Protect Enterprise Cloud
