Towards a Dynamic Controller Scheduling-Timing Problem in Software-Defined Networking
2017-04-08ZhenpingLuFucaiChenGuozhenChengChaoQiJianjianAi
Zhenping Lu, Fucai Chen, Guozhen Cheng, Chao Qi, Jianjian Ai
National Digital Switching System Engineering & Technological R&D Center Zhengzhou 450002, China
* The corresponding author, email: 2011301200300@whu.edu.cn
I. INTRODUCTION
Software-Defined Networking (SDN) is a novel architecture that has been designed to capacitate more alive and loss-efficient networks and provides a service-oriented architecture to deploy modular solutions to meet different requirements. In the future, SDN looks forward to becoming a $70.4 billion market by the year 2024. Deploying SDN in data center is an excellent way to promote bandwidth utilization in business network (e.g., Google B4 [1]). No doubt that, there is a serious security breach in SDN. Most notably, the controller is the brain in SDN, which may make it easy to manage network, but also tends to be attacked. It is very likely that the entire network will be paralyzed because the controller is compromised or hijacked [2]. This is simply the inherent weakness of SDN, and no solution has been provided until now.
Recently, in order to increase the difficulty and uncertainty of the adversary assault, introducing dynamic and multiple controllers to deploy the control plane is a good way to mitigate the effect of some attacks. However,the existing researches in dynamic controller architectures are mostly devised from the perspective of scalability, efficiency and avail-ability instead of security. Although they can enhance security of controller to some extent,they can hardly deal with specific attacks such as Flow Rule Modifi cation attack. Especially the elastic distributed control plane [3] can adjust the controller instances dynamically according to the changes of network loads.Although ONOS [4]and OpenDaylight [5]employ multiple controllers to act as various roles in case master controllers paralyse, backup controllers are converted to master controllers to maintain the network operate. These distributed architectures have dynamic to some extent, but they don’t take the attacker into consideration. The controller instances in the mainstream distributed architecture, however,are still homogeneous, which consequently results the fact that these controllers possess the same vulnerabilities. Once the attacker finds one vulnerability, it will easily affect the entire distributed control plane. Dixit et al. [6] propose an efficient protocol to enable controller migration across multiple switches without message loss or observable delay for shorter controller response time and better utilization of controller resources.
However, dynamic techniques for security in control plane have been considered in only a few works. The works in [7][8][9][10]discuss the potential benefits and the scope of using dynamic controller. For instance, wang et al. [7] attempt to deal with load balance among controllers via dynamic controller assignment, which achieves the goal of satisfying performance and enhancing the security level in some extent. In the context of control plane security, Eldefrawy et al. [8] propose a prototype SDN controller to tolerate Byzantine faults both in the control and data planes.This design can handle single point of compromise and failure via dynamically mapping one switch to multiple controllers to construct resilient programmable networks. Li et al. [9]present a secure SDN structure, in which each device is managed by multiple controllers, not just a single as in a traditional manner, with the dynamic and isolated instance provided by the cloud. It can resist Byzantine attacks on controllers and the communication links between controllers and SDN switches. Qi et al. [10] design a framework called Mcad-SA with multiple NOSs to defense the modifying flow rule attack. Furthermore, he puts forward a dynamic scheduling method to maximize security gain of NOS during each switch [11].Hu et al. [12] also generally indicate that a dynamic controller mechanism which dynamically changes multiple controller of SDN is designed to raise the bar for their successful attacks and the security of control plane, and thus increases the complexity and uncertainty of discharging the attack target, increases their cost of probing and attacking.
In general, most of the existing researches for security in dynamic control plane have started to focus on deploying different several mechanisms to enhance the safety levels for defender. However, it would result in expense for the service providing in the protected SDN during each scheduling. Frequent scheduling will lead to remarkable slowdowns in performance, while insufficient scheduling can’t effectively hinder potential adversaries, which is yet a dilemma. Little work has been done on determining the optimal time of scheduling controller. To understand the importance of scheduling timely in control plane, we present the three defense scenarios in figure 1. Typically, there are four attack phases for an attack over control plane: fingerprint, targeting vulnerable machines, finding exploits, and launching effective attacks [13]. As for the dynamic control plane, these defense mechanisms are as follow: (1) Without scheduling. (2) Stupid scheduling. (3) Intelligent scheduling.
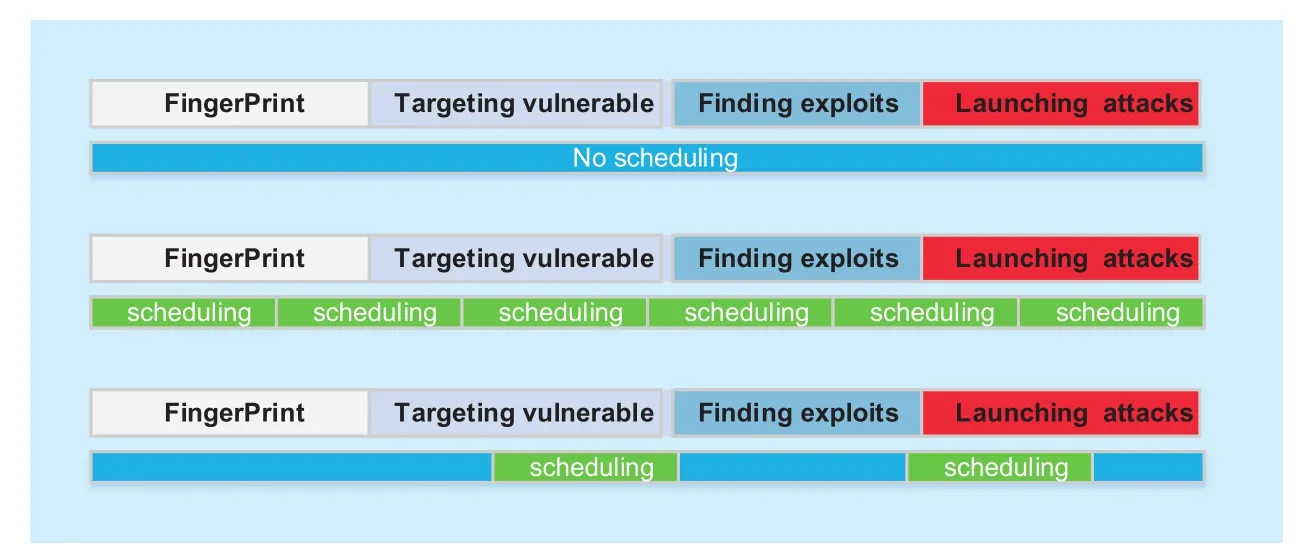
Fig. 1 The scheduling-timing determination in various defense mechanisms
From this figure, if the defender only patch against threats on controllers without a rotation, it will enable attackers to probe without time limits under such circumstance.Furthermore, both stupid scheduling and intelligent scheduling may effectively mitigate the attacks by making rotation before an attack is launched. However, stupid scheduling continually isn’t rational as it leaves the power or frequency of adversaries out of consideration. Moreover, it can be a heavy burden for services especially when it is expensive to rotate controllers. Thus, determining the right time to rotations is crucial between dynamic-scheduling controllers more loss-efficient and reducing the service overhead brought by dynamism.
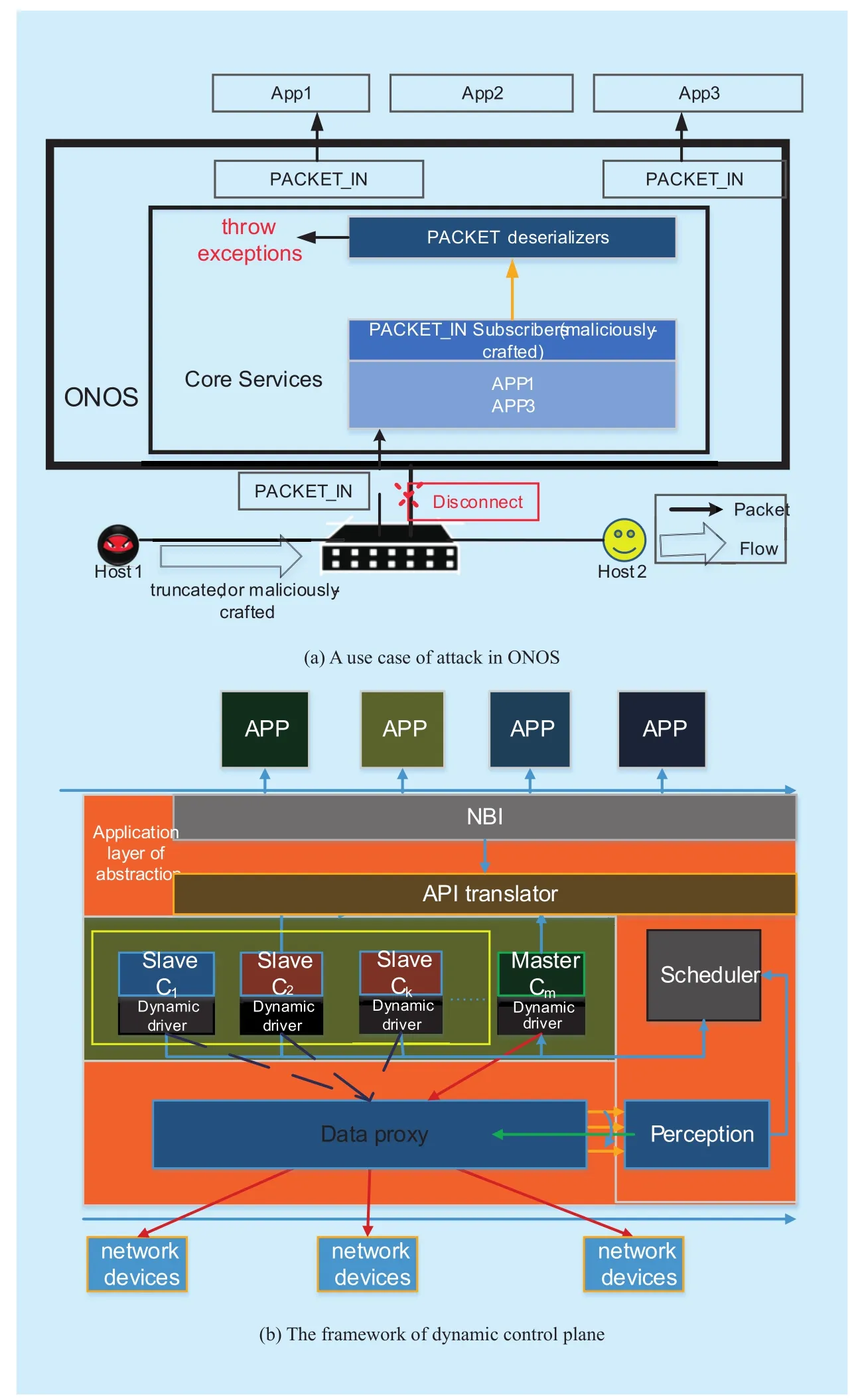
Fig. 2 An attack example and the defense mechanism of dynamic controllers
This work extends our prior work in [14].To the best of our knowledge, this is the first step to both theoretically and experimentally investigate the scheduling-timing problem,which in our study refers to the best time to schedule controllers. We take account of both attacked loss and scheduling loss from defender’s to determine the best time to schedule controllers from the defender’s perspective.Our proposed algorithm not relies on any traditional passive defense techniques in making scheduling, but proactively calculates the appropriate scheduling time through the historical attack intervals. The objective is to design a scheduling strategy that guides the dynamic mechanism to make scheduling in the right way to minimize the overall loss rate. The basic idea of we further solve this problem is to balance both scheduling loss and the attacked loss based on the renewal reward theory.
II. SYSTEM ARCHITECTURE AND THREAT MODEL
In this section, we first present the previously proposed SCP framework and describe a threat model to characterize the dynamic-scheduling controllers. This theoretical framework follows the state-of-the-art model proposed by Zhuang et al. [15]. Specifically, we introduce an attack-defense scenario in which defenders employ dynamic mechanisms, while attackers exploit the vulnerability of defenders to launch attacks.
We extend the control layer of SDN to assist the deployment of virtual functions in SCP[14] as figure 2(b). The constitution and functions are described below.
First, the data proxy collects the information of data plane and delivers them to control plane. The perception claps eyes on anomaly detection at the same time. The scheduler selects Master controller which sends the valid instructions to network devices. Then, once any mechanism of the scheduler is activated,new Master will be elected. And if perception tells anomaly to scheduler, the scheduler will shut down the corresponding Master and pick the new Master from executive resource next time. Otherwise, there is no extra adjustment needed to be done. Finally, above actions will be repeated to keep the control plane in a secure, robust and resilient state.
An attack scenario as figure 2(a). ONOS is an Open Network Operating System based on OSGI using Java, which brings about the vulnerabilities of OSGI. Figure 2 shows an attack aimed at ONOS [16]: When ONOS receives a packet-in, it tries to deserialize the packet into an Ethernet object. As it has been mentioned earlier, when an OpenFlow switch encounters a packet that does not match any forwarding rules, it passes this packet to the controller for advice. It was found that the packet deserializers in ONOS would throw exceptions when handling malformed, truncated, or maliciously-crafted packets. The exceptions were not caught and handled, which would result in the relevant switch being disconnected because an exception occurred in an I/O thread. A remote attacker (Host 1) could use this flaw to perform a DoS attack by causing ONOS to disconnect switches. For an attacker to exploit this flaw, it only needs to be able to send malicious crafted packets through a switch controlled by ONOS. This is an example of how the data plane can be used to make full use of the flaw on the controller. If it is static mappings between the control plane and data plane, an adversary will be able to take advantage of the vulnerability all the time.
Defense action. If Ryu or Floodlight becomes the Master controller to manage the network according to the scheduling mechanism in figure 2(b), the above attack action aimed at ONOS will be in vain due to the fact that Ryu or Floodlight is not adopted OSGI framework. The dynamic control plane not only has access to defend the vulnerabilities of controllers but also it is capable of defending the Man-In-The-Middle and Flow Rule Modification attack [11][12].
Despite the advantage that the framework enhances the safety levels of control plane, the scheduling mechanism lead to the loss of network at the same time beyond all doubt. Our objective is to design a scheduling strategy that guides the dynamic mechanism to make scheduling in the right way to minimize the overall loss rate. The threat model is as follows.
Defenders
Definition 1.The critical information parameter (CIP). It should be noted that CIP refer to the information parameters defined for a controller. In order to increase the success of attack, the adversary usually gathers some information of control plane in advance,including the IP address of the controller, the workload, and the controller types, etc. What the attackers need before conducting an attack is called the critical information parameter.
By collecting the CIP, an adversary launches a purposeful action. For example, timing attack sends both probing packets and testing packets to evaluate the workload of controller[17], then it carries on DDoS attack effectively. If an adversary explore the controller’s IP,the normal user will be likely to have the session hijacked [2]. Conversely, defender aims at reducing the amount of CIP that the attacker can take advantage of by probing.
Definition 2. Scheduling loss. In order to reduce the probability of successful attack,scheduling controller during each rotation will lead to the temporary reduction of network system performance and service quality
Using dynamic mechanism, a defender can make rotations to change the CIP. For each rotation, it triggers a scheduling loss, which includes the loss of time and money, such as the missed new flows caused by restarting to establish the mapping between the new controller and the data plane (learning port and host location), purchasing various merchant controllers, renting IP addresses and the loss of possibly temporarily slowing down the sys-tem performance during the rotation [18].
Adversaries
An adversary with the purpose of destroying or getting the confidentiality, integrity and availability (CIA) of targets is diametrically opposed to the defender.
In general, according to the theory of Attack Chain, the adversary first needs to fingerprint the CIP at the expense of time and computing or monetary resources to aggrandize successful probability. Nevertheless, once the attack succeed, there will be an attacked loss burdening on the defender. The attacked loss is closely related to the CIP of the defender as well as the attack types. For example, the more controller manages switches or hosts, the larger loss caused by DDoS [19].
In researching the scheduling-timing problem of dynamic-scheduling controllers, we explore a series of attacks concerned. In such attack-defend condition, the probing time for an attacker to make a successful attack,after a defender launches a rotation, satisfies identical and independent distributions [18].This closely concerned attacks include covert channel attacks in the cloud [20], IP scanning and stealthy port scanning [21], and password cracking [22], etc.
Goal. The goal of studying the scheduling-timing problem is to finger out the most loss-efficient approach for a defender to conduct rotations, considering both the scheduling loss and the attacked loss.
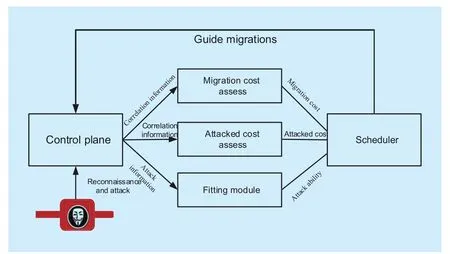
Fig. 3 work flow of the SCP framework
It is quite reasonable in this circumstance:If the scheduling loss is high while the attacked loss is low, the defender will bear the risks of being attacked instead of making a rotation. In the case, we plan to deal with the problem of what is or figure out the best time to rotate controllers in order to minimize the loss rate.
III. WORKFLOW AND ALGORITHM DESIGN
In this section, we first present the work flow in which an algorithmic approach to the scheduling-timing problem can work on top of that. Then we present our algorithm in detail,which effectively determines the loss-efficient scheduling time for the defender.
3.1 work flow
The defense mechanism is described below:
Control plane (Defender system). The control plane has the objective of protecting itself from being attacked in a loss-efficient manner. In order to achieve the objective, it makes rotation between various controllers under the guidance of the scheduler.
Scheduling loss assess. Scheduling loss assess component measures and calculates the scheduling loss based on the CIP of the defenders. Scheduling loss is the overall loss incurred to the defender system when it goes from one controller to another.
Attacked loss assess. Attacked loss analysis component measures and calculates the attacked loss based on the CIP of the defenders,as well as the services currently running in the APP plane. In general, the attacked loss should be calculated in an online manner since the set of services may vary over time and so does its loss.
Fitting module. The fitting module fits the historical attack intervals to find out a distribution pattern of the attacks. It provides knowledge about the distribution of the attack time intervals. This information is useful and critical in calculating the appropriate scheduling time to balance the scheduling loss and attacked loss for a defender. Note that this distribution may not necessarily satisfy a predefined probability distribution, but it should be identical and independent distributed.
Scheduler. The scheduler is to predict the time of next rotation. It takes the scheduling loss, the attacked loss, and the historical attack time intervals into account, and decides the most loss-efficient time to schedule. The decision is made by formulating the scheduling-timing problem as a renewal reward process and we solve the problem using the renewal reward theory [23]. The details of the algorithm are discussed in Section 2.
3.2 Algorithm design
Table 1 shows the key notations of this paper.In this section, we design an optimal scheduling algorithm based on the renewal reward theory for the defender to determine the best scheduling time through algorithm 1.The steps are as follows.
We name our algorithm OSA (standing for optimal scheduling algorithm), which is illustrated in algorithm 1. OSA aims to determine the optimal scheduling time in the longterm process, subject to the above-described notations. The procedures of this scheduling algorithm are shown in algorithm 1 which illustrates the dynamic scheduling process is a long-term process (as shown in the while loop in Line 1). And after each scheduling of the defender, the algorithm determines when to make the next scheduling to be loss-efficient by calling a procedure named DST (see algorithm 2).
Algorithm 1 illustrates the defender measures the scheduling loss and attacked loss based on the CIP of control plane respectively for a long-term process in detail. Then it calculates the scheduling time using algorithm 2. However, if the attack occurs before the T(in line 6), scheduling controller need to be launched immediately. In step 6, we assume that a defender can estimate whether an attack happens through the anomaly intrusion detection mechanisms or other methods [24].
Note the following about algorithm 2. Algorithm 2 illustrates the steps of obtaining theloss-efficient scheduling time. The problem is modelled classically as a renewal reward process to determine optimal scheduling time for the sake of the overall loss. T can be deal with by the following Equation (7) in Algorithm 2.
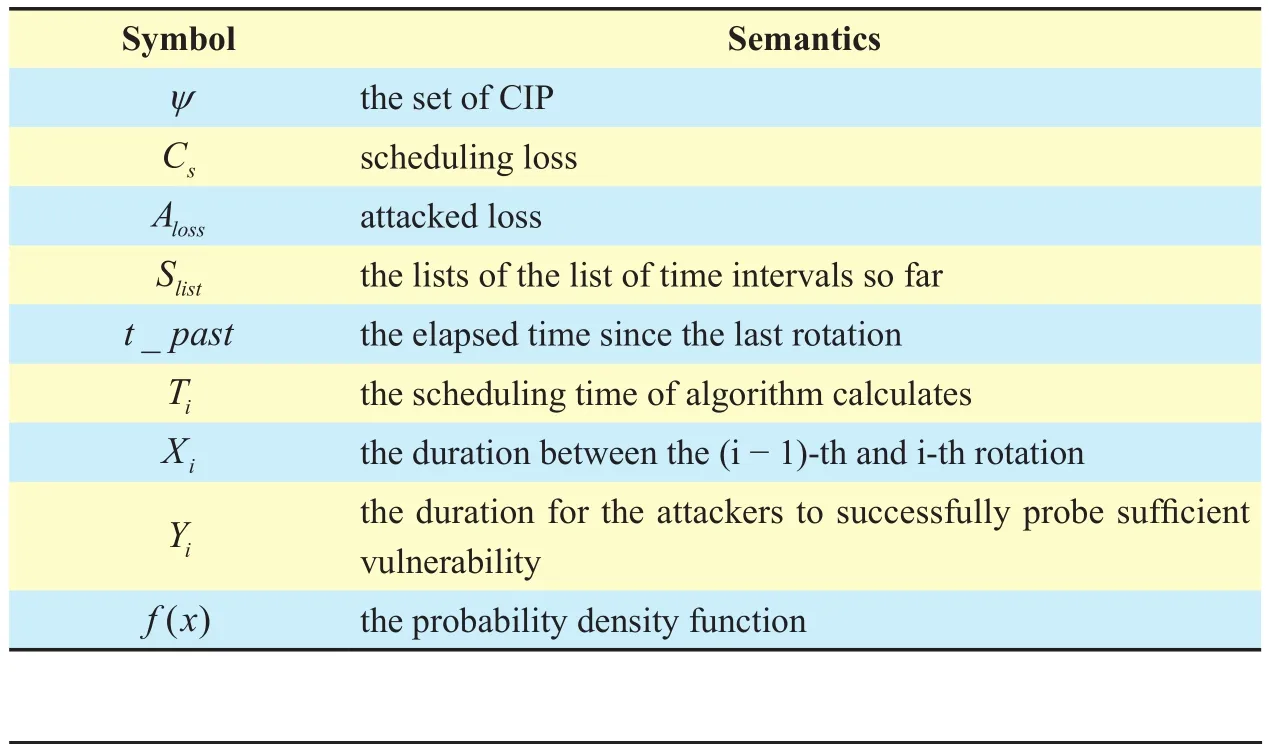
Table I Key notations
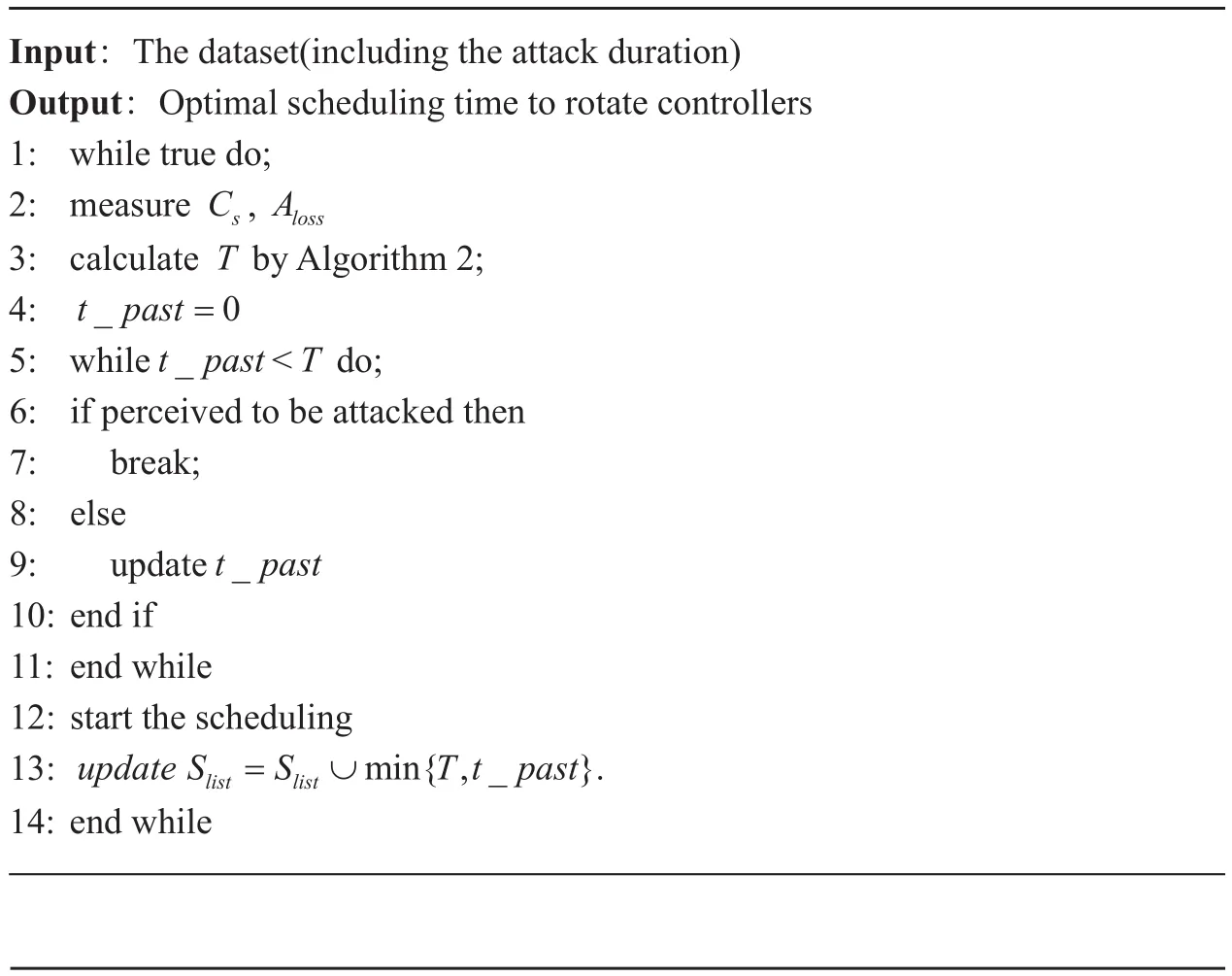
Algorithm 1 Optimal scheduling algorithm

Algorithm 2 Determining scheduling time algorithm (DST)
Theorem 1. For a series of attacks with their attack time interval lengths satisfying identical and independent distributions, there is an optimal algorithm to determine the optimal scheduling time for the purpose of minimizing the long-term loss.
We remark that the attack time duration lengths are values from a continuous real region.
Proof. The dynamic-scheduling course in nature is a stochastic process in which rotations happen over time. Specifically, the scheduling process can be modelled as a renewal process that each scheduling can be regarded as a ‘restart’ of the process during which the defender waits for the next scheduling. Thus, we formulate the scheduling-timing problem as a renewal process with the objective to decide the ‘renew’ time that is most loss-efficient.
We consider the stochastic process in which a defender schedules controllers over time.The loss of scheduling controllers is portrayed as a function of the time of when to schedule.For a defenderd, let Xidenote the duration between the i−1-th and i-th rotations. Let Yidenote, after thei-th scheduling of the defender, the duration for adversaries to successfully reconnaissance sufficient vulnerability of the defender to launch an attack. Assume Yihas a distribution Fd, the corresponding probability density function isfx() : the probability that an adversary spends time x to probe sufficient vulnerability, which is historical-based. The cumulative density function is thus

If d is being attacked, in which case, it will pay an additional expense:Aloss. Furthermore, it should schedule a new controller to take over the network. Meanwhile, scheduling brings about scheduling loss, denoted as Cs.Thus, we have
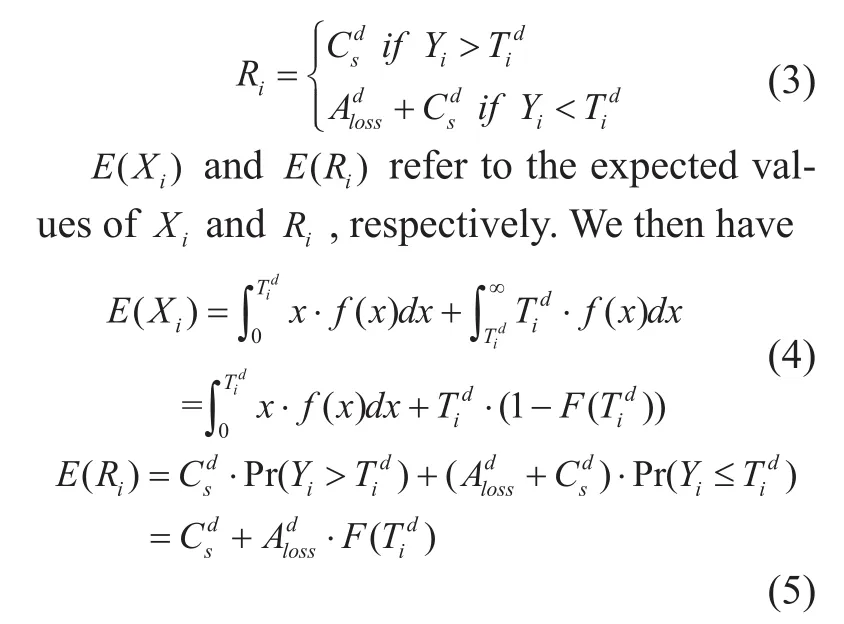
Definition 3. Loss rate. The actual loss is divided by the actual scheduling loss during the duration between the i−1th and i-th scheduling.

Thus we can obtain the optimal time to make scheduling.
IV. PERFORMANCE EVALUATION
In this section we will analyze the loss-efficient performance of the proposed OSA algorithm against attacks based on real attack datasets. The experiment was carried out on a mainframe with Intel (R) Core (TM) i7-4790 CPU 3.6 GHz, 4GB RAM. First, we describe the experimental settings and utilize SPSS to determine the distribution of attack interval. Then we run the OSA algorithm on the platform called Mathematica. Finally, we measure the loss efficiency of our proposed OSA algorithm using real attack datasets with comparisons to existing strategies, including up-to-date periodical scheduling strategies and a randomized scheduling strategy.
4.1 Experimental settings
We use the datasets provided by the third party as input data [25], which consists of the detailed research information, such as the adversary identity, the defender IP address, and the historical attack time. In order to characterize the long-run cost efficiency of different dynamic algorithms, facilitate the research and ensure great credibility, we select a total of 151 datasets with each dataset including more than 30 times of attacks the input of simulation.
Topology. We conduct our simulations by using three different topologies with 50 switches, 100 switches, 200 switches, respectively. Each switch is connected with 2 hosts.We have used the Mininet simulators and built three various topologies in the Python languages.
Sampled Dataset. We fit Kolmogorov Smirnov method to the time interval of sampled dataset based on SPSS software. We study the goodness-of-fit of normal distribution, exponential distribution, uniform distribution and Poisson respectively, the results in table 2 show that more than 100 attack interval is accord with normal distribution at 0.05 significant level, the other is not in conformity with any distribution. When the level of significance is set to 0.1, almost all is in a log-normal distribution. This is consistent with the rule that the duration distribution of attack time in theorem 1 corresponds to independent distribution.
Attacked loss and Scheduling loss. We now are ready to describe the function ofMeasuring attacked loss and scheduling loss is extremely difficult due to the lack of respective ideas. Facing the various attack threats, different groups usually pay different prices. For some large enterprises, it is common for it to set up a specific security organization to conduct attack analysis and loss evaluation. While for small organizations or individuals, some tools have been developed and made available for them to measure the attacked loss[18]. To simplify the process or procedure, we assumeare both related to the size of network topology and total rate of new flow requests[26].
Definition 4. Network throughput rate. Different from the throughput rate according to the packets in traditional network, controllers in SDN, in particular, may perform more advanced flow processing as needed, especially when packets of a new flow arrive at a switch that does not have a matching rule installed.Hence, we regard arrival rate of new flow requests in each switch as the throughput rate of each node, denoted as qs. The overall throughput rate (Qtp) is the sum of whole switches.

For simplicity, we suppose the processing capacity of every switch is same, and the arrival rate of new flows for a host is subject to poisson distribution.
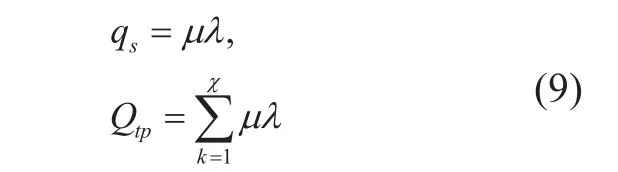
u represents the number of hosts connected by the a switch. χ denotes the number of switches in network.
There is no doubt that the larger topology is, the moreare. Furthermore,in SDN network, once scheduling controller occurred, the new flow requests would have been dropped out since the controller couldn’t deal with the requests timely, whereas the past flows could be transmitted since these flow rules have been already installed in the switches. Similarly, the new flows can be dropped out or be probed when the controller is under being attacked. Here, we adopt the simplest linear form of
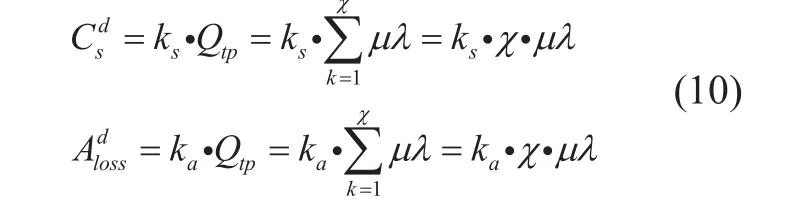
In this paper, in order to facilitate research,we assume that ka=5, ks=3 is an example to assess the attacked loss and scheduling loss,respectively. We simulate the performance under three different topologies by varying flow arrival rate (namely, varying the λ ).
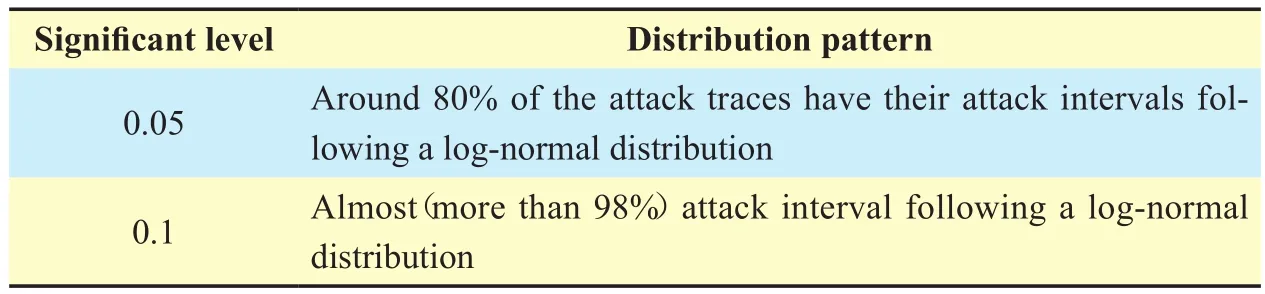
Table II The relationship between significant level and distribution pattern
Definition5. Effectiveness coefficient. Defenders dynamically change the CIP of control plane to invalidate the information gained by an adversary who is forced to frequently redo the reconnaissance activities to regain the lost information to launch an attack. Effectiveness coefficient is to measure the effect of dynamic mechanism,

Due to the limitation of the datasets, we are not aware whether defenders in the datasets have employed dynamic mechanisms or not.This issue matters as our proposed algorithm is dedicated for defenders to use under the scheduling scheme. In essence, our designed algorithm aims to assist in making decisions about the right scheduling time in the dynamic condition. Thus we consider the following two cases.
Case1: In the collected datasets, the defender implemented the dynamic-scheduling mechanisms.
We use the original attack datasets to simulate the attacks in the simulation.
Case2: In the collected datasets, the defenders didn’t implement the dynamic-scheduling mechanisms.
Specifically, if defenders defend againstattacks by making dynamic scheduling, adversaries will have to restart the fingerprint procedure to regain current controller’s CIP (e.g.IP scanning), which delays the arrival of next attack. Thus, we increase the time between two successive attacks in the attack datasets to reflect the effects of dynamic-scheduling controllers. In the simulation, we study the loss efficiency under the attack datasets with various effectiveness coefficients.
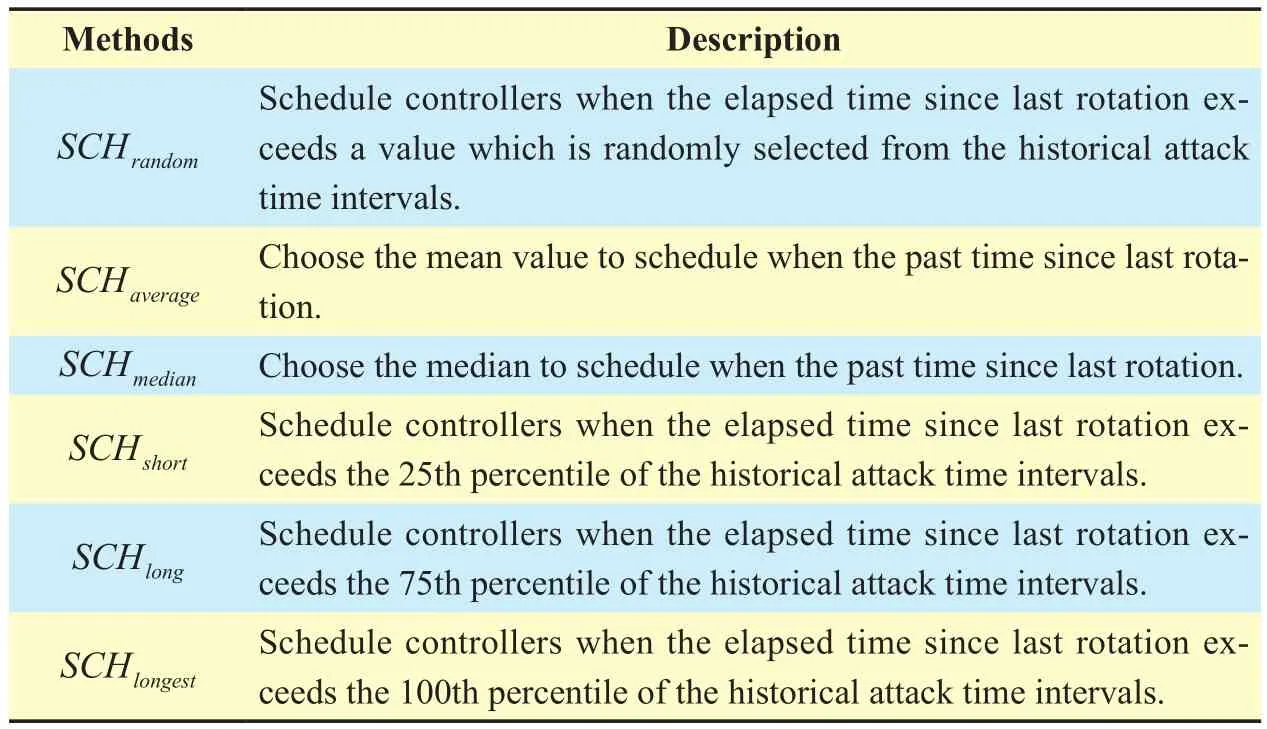
Table III Various scheduling methods
In the simulation, we compare our proposed algorithm OSA with the up-to-date periodically scheduling algorithms which is common in control plane. In addition, a randomized algorithm is introduced for comparison. Table 3 is the description of all the algorithms.
Long-term loss rate. For each defender,we record the scheduling loss and the attacked loss it suffers under different scheduling methods separately in the simulation. The elapsed time for each defender is also recorded during the simulation. Then the long-term loss rate of
4.2 Evaluation Result
4.2.1 Evaluation of loss efficiency
We simulate different methods under different settings of scheduling loss (topology and λ,respectively), and compare the average longrun loss rate of all the defenders.
Figure 4 and 5 show the long-run loss rate of all defenders according to different methods, with the topology is set as 50,100,200 and λ is set as 0.5,1,5, respectively. In particular,figure 4 uses the original attack datasets as the attack inputs, while figure 5 uses the original attack datasets with effectiveness coefficient set as 2.
Figure 5 illustrates that the performance of above strategies is similar to figure 4, since the topology and the value of λ are in com-plete equality as the throughput coefficient. As mentioned in the table 4, the result indicates a random algorithm or fixed-cycle methods is not capable of trading off the scheduling loss and attacked loss. OSA is likely to perform a better long-term average loss rate than other methods. In conclusion, OSA is more economical compared with random or fixed-cycle methods.
Next, we study another question regarding our results: whether the advantages of our algorithm are robust? By varying thebetween the range of [0.2,3.5], we compute the average loss rate of all defenders under various topologies with λ=1. The result is illustrated in figure 6. It indicates that advantages of our algorithm always are significantly robust in different practical environments.
4.2.2 Effectiveness coefficient
According to figure 4 and figure 5, modifying the input datasets of attack with setting effectiveness coefficient as 2, the loss rate is nearly decreased by half. It is because with effectiveness coefficient set as 2, the attack time durations are going to double, while the scheduling loss and attacked loss stay unchanged. While the loss that a defender suffers might be affected as the distribution fitting under the modified attack datasets might be different, which could affect the scheduling time for OSA. Based on the considerations above, we further study the relation between the long-run average loss rate and the effectiveness coefficient.
We conduct simulations to study the long-run loss rate under various effectiveness coefficients using our proposed OSA algorithm as an example. The study results are shown in figure 7.
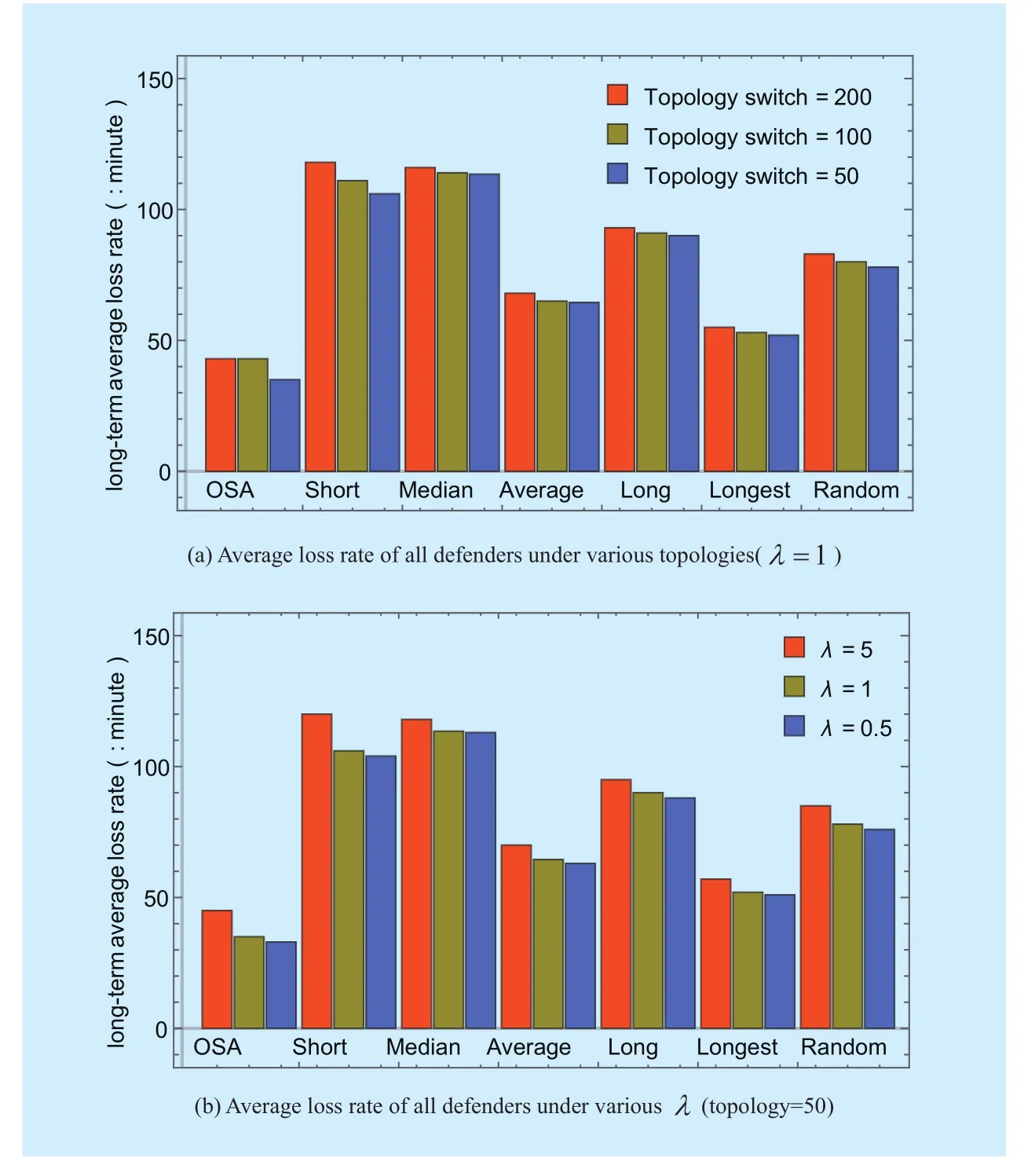
Fig. 4 Average loss rate of all defenders of attack datasets with original attack datasets
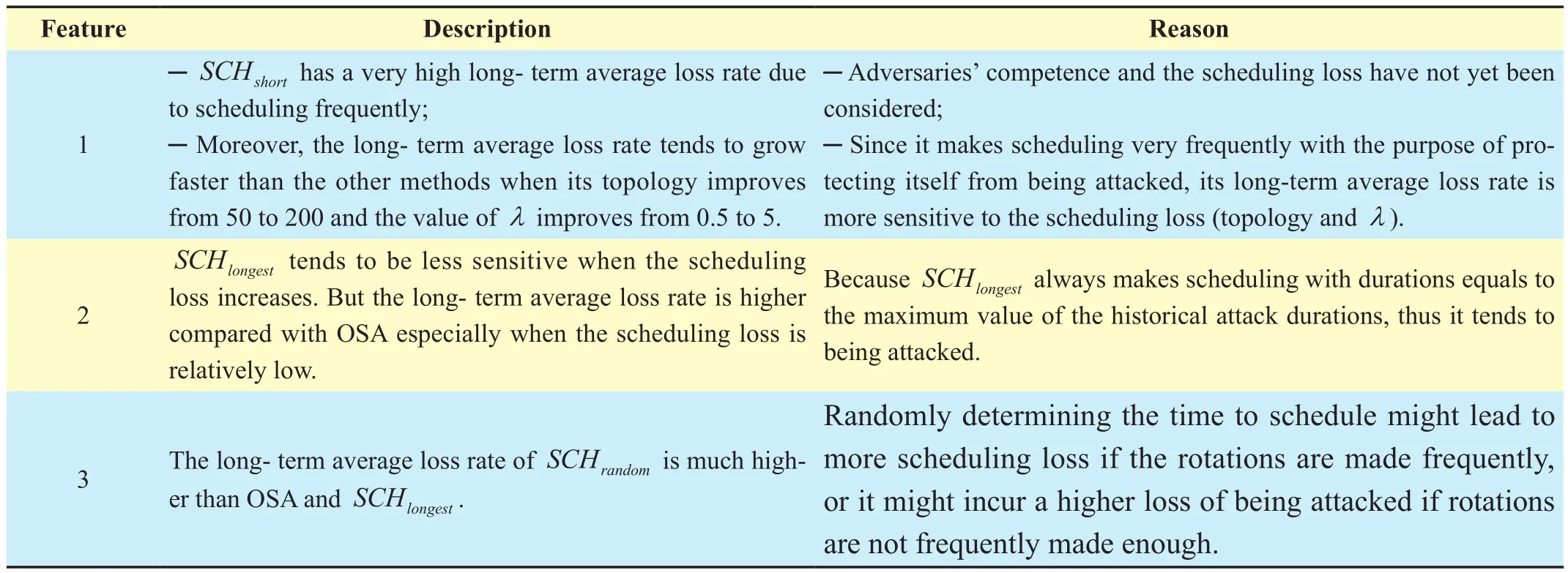
Table IV Some obvious characteristics of different methods
Figure 7 illustrates average loss rate under OSA algorithm with the topology set as 50 and λ=1. The x-axis and y-axis show the effectiveness coefficient and the corresponding long-run loss rate respectively. According to the figure, the long-run loss rate reduces at almost the same speed as the effectiveness coefficient grows. This result indicates if the defender can find a dynamic-scheduling mechanism to delay the attack as much as possible,it can decrease the long-run average loss rate accordingly.
4.2.3 Scheduling duration
In the following, we study the scheduling time of various methods under various scheduling loss () settings. We conduct simulations in which defenders making decisions based on each algorithm. We record the scheduling time under each algorithm and compute the average value in figure 8.
In figure 8, the x-axis demonstrates the scheduling loss range, and the y-axis shows the corresponding average scheduling time duration following each method. From the figure,we can infer that the OSA algorithm is likely to have a larger average scheduling duration due to the scheduling loss increases. This shows that when the scheduling loss is high, it is no longer loss-efficient for making rotation frequently. However, as other methods make scheduling decisions without considering the loss, the average scheduling time under these methods is not affected by the scheduling loss.
V. CONCLUSION
Deploying dynamic controllers in SDN is an effective way to mitigate many security threats of the control plane. It works by changing a control plane’s attack surface dynamically and thus increases the difficulty of successful attacks. In this paper, we study the scheduling-timing problem about how to determine the optimal time to schedule controller based on the prior work. We model this problem as a renewal reward process and propose an optimal algorithm in deciding the right time to schedule with the objective of minimizing the long-term loss rate, which trade off the loss of scheduling controller and the loss of being attacked. The result demonstrates that our proposed algorithm outperforms known scheduling schemes. As for future work, more comparisons against other scheduling strategies will be conducted, and measuring the attacked loss and scheduling in detail is an interesting and meaningful research topic.
ACKNOWLEDGMENT
This work was supported by the Foundation for Innovative Research Groups of the National Natural Science Foundation of China (No.61521003), The National Key R&D Program of China (No.2016YFB0800101), the National Science Foundation for Distinguished Young Scholars of China (No.61602509) and Henan Province Key Technologies R&D Program of China(No.172102210615).
[1] Jain S, Kumar A, Mandal S et al., “B4: experience with a globally-deployed software defined wan,”Proc. ACM SIGCOMM Computer Communication Review, 2013, 43(4):3-14.
[2] Brooks M, Yang B et al.,“A Man-in-the-Middle attack against OpenDayLight SDN controller,”Proc. ACM Conference on Research in Information Technology. ACM, 2015:45-49.
[3] Krishnamurthy A, Chandrabose S P et al.,“Pratyaastha: an efficient elastic distributed SDN control plane”Proc. The Workshop on Hot Topics in Software defined NETWORKING. ACM,2014:133-138.
[4] Berde P, Hart J, Hart J et al., “ONOS: towards an open, distributed SDN OS,” Proc. The Workshop on Hot Topics in Software Defined NETWORKING. ACM, 2014:1-6.
[5] Medved J, Varga R, Tkacik A et al., “OpenDaylight: Towards a Model-Driven SDN Controller architecture,” Proc. World of Wireless, Mobile and Multimedia Networks. IEEE, 2014:1-6.
[6] Dixit A, Hao F, Mukherjee S et al., “Towards an elastic distributed SDN controller,” Proc. Computer Communication Review, 2013, 43(4):7-12.
[7] Wang T, Liu F, Guo J et al., “Dynamic SDN controller assignment in data center networks: Stable matching with transfers,” Proc. IEEE INFOCOM 2016 - the, IEEE International Conference on Computer Communications. IEEE, 2016:1-9.
[8] Eldefrawy K, Kaczmarek T et al., “Byzantine Fault Tolerant Software-Defined Networking (SDN)Controllers,” Proc. Computer Software and Applications Conference. IEEE, 2016:208-213.
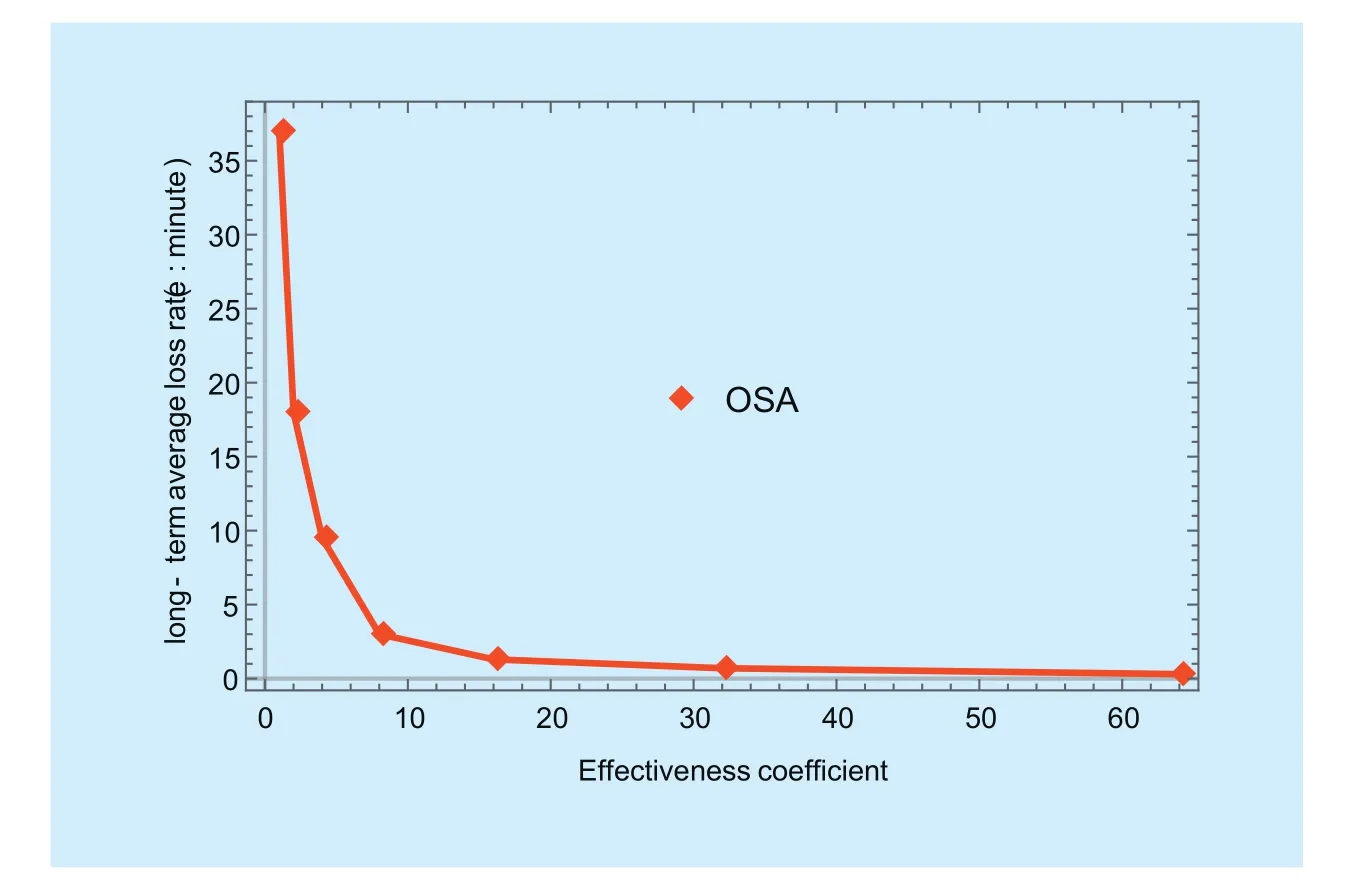
Fig. 7 Loss rate vs. effectiveness coefficient under OSA algorithm with the topology set as 50 and λ=1
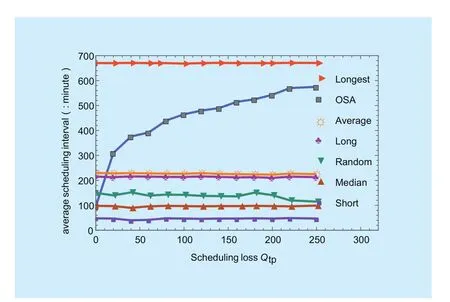
Fig. 8 Average scheduling time. effectiveness coefficient = 1
[9] Li H, Li P, Guo S et al., “Byzantine-Resilient Secure Software-defined Networks with Multiple Controllers in Cloud,” Proc. IEEE International Conference on Communications. IEEE, 2014:695-700.
[10] Qi, C et al., “An intensive security architecture with multi-controller for SDN,” Proc. INFOCOM Posters, 2016.
[11] Qi C, Wu J, Hu H et al., “Dynamic-scheduling mechanism of controllers based on security policy in software-defined network,” Electronics Letters, 2016, 52(23):1918-1920.
[12] Hongchao Hu, Zhenpeng Wang, Guozhen Cheng et al., “MNOS: A Mimic Network Operating System for Software Defined Networks”,IET Information Security, DOI: 10.1049/ietifs.2017.0085, 2017.
[13] Zhuang R, Deloach S A et al., “Towards a Theory of Moving Target Defense,” Proc.ACM Workshop on Moving Target Defense. ACM, 2014:31-40.
[14] Z. Lu, F. Chen, J.Wu et al., “Poster: A Secure control plane with Dynamic Multi-NOS for SDN,”Proc. Network and Distributed System Security Symposium (NDSS), February 2017.
[15] Zhuang R, Bardas A G, Deloach S A et al., “A Theory of Cyber Attacks:A Step Towards Analyzing MTD Systems,” Proc. ACM Workshop on Moving Target Defense. ACM, 2015:11-20.
[16] “Exceptions thrown while deserializing truncated or malformed packets,” https://jira.onosproject.org/browse/ONOS-605.
[17] Sonchack J, Aviv A J et al., “Timing SDN Control Planes to Infer Network Configurations,” Proc.ACM International Workshop on Security in Software defined Networks & Network Function Virtualization. ACM, 2016:19-22.
[18] Wang H, Li F, Chen S et al., “Towards Cost-Effective Moving Target Defense Against DDoS and Covert Channel Attacks,” Proc. ACM Workshop on Moving Target Defense. ACM, 2016:15-25.
[19] ECESSA et al., “What does network downtime &latency cost your business,” http://www.ecessa.com/blog/downtime-costs/, 2014.
[20] Ristenpart T, Tromer E, Shacham H et al., “Hey,you, get oあ of my cloud: exploring information leakage in third-party compute clouds” Proc.ACM Conference on Computer and Communications Security. ACM, 2009:199-212.
[21] Jafarian J H, Al-Shaer E et al., “Adversary-aware IP address randomization for proactive agility against sophisticated attackers,” Proc. Computer Communications. IEEE, 2015:738-746..
[22] Weir M, Aggarwal S, Medeiros B D et al., “Password Cracking Using Probabilistic Context-Free Grammars,” Proc. IEEE Symposium on Security &Privacy. IEEE Computer Society, 2009:391-405.
[23] Ross S M et al., “Introduction to probability models,” Technometrics, 2010, 82(1):625-627.
[24] Lee S, Yoon C et al., “DELTA: A Security Assessment Framework for Software-Defined Networks” Proc. Network and Distributed System Security Symposium (NDSS), February 2017.
[25] Wang A, Mohaisen A, Chang W et al., “Delving into Internet DDoS Attacks by Botnets: Characterization and Analysis,” Proc.Ieee/ifip International Conference on Dependable Systems and Networks. IEEE, 2015:379-390.
[26] J Sonchack, AJ Aviv et al., “Enabling Practical Software-defined Networking Security Applications with OFX,” Proc. Network and Distributed System Security Symposium (NDSS), February 2017.
杂志排行
China Communications的其它文章
- Migration to Software-Defined Networks: the Customers’ View
- Software Defined Traffic Engineering for Improving Quality of Service
- Efficient Virtual Network Embedding Algorithm Based on Restrictive Selection and Optimization Theory Approach
- A Fast and Memory-Efficient Approach to NDN Name Lookup
- Energy-Efficient Joint Content Caching and Small Base Station Activation Mechanism Design in Heterogeneous Cellular Networks
- Dual Power Allocation Optimization Based on Stackelberg Game in Heterogeneous Network with Hybrid Energy Supplies
