Attack Technology Research for Web Service
2014-09-14SUGuangnanFENGYongxin
SU Guangnan,FENG Yongxin
(Shenyang Ligong University, Shenyang 110159,China)
Web service is a platform-independent,loosely coupled,self-contained,web-based programmable application that uses open XML standard to describe,publish,discover,coordination and configure the applications for the development of distributed interoperable applications[1].Because of its run on different machines enables different applications without the aid of additional,specialized third-party software or hardware,you can exchange data with each other or integrated,making the current Web services technology has become the most widely used techniques.But with the increase infrequency of use,Web service is increasingly obvious shortcomings.The providers and users of Web services are from different places,and the message is transmitted through the public network,will inevitably result in loss,theft,tampering of information.Also,because some protocols of Web services support in the formulation does not consider safety measures,resulting that some of the attacks on the service itself cannot effectively resist[2-3].In this paper,the attack technique principles of the Web service expounded,and buffer overflow attacks,flooding attacks,XML data recursion attack are simulated,and thus provide a reference to improve the Anti-aggressive and Immunity of Web service.
1 CLASSICAL ATTACK METHODS
The classical attack methods of Web services include the following[4-7]:WSDL scan:WSDL description contains the functions,parameters and return values of the service,attackers can obtain service information by WSDL scanning.Deliberate error message:the attacker constructs an error SOAP message to make the server abnormal,through the analysis of the message that the server returns under abnormal condition,informed of the unpublished information.Code attacks:the attacker archive the distal user′s password by listening,exhaustive crack,Trojan,and then get authorities of current user.Buffer overflow attack:attackers using buffer overflow vulnerability,by writing shellcode,to attack the server,and after the success of buffer overflow attack,the attacker archive all the authorities of current user.SOAP flooding attacks:attackers send the server a lot to the SOAP message which conform the format requirements,to make the server resource depletion,refuses to accept the same message,and lead to the effect of denial of service.XML recursion data attack:attackers structure a deeply nested XML document and send to the target server,when the host parses the XML document,it will occupy a lot of computing resources and memory resources,and lead to the effect of denial of service.SQL,XPath injection:some server lack of detection mechanism of the input data,causing the attacker can illegal complete various operations to a data store by injecting the data manipulation language,and these will lead to the effect of archiving authority or tampering with data.Cross-site scripting attack:the attacker on the dynamic site there are loopholes in the injected malicious code,when users click Connect with malicious code,the attacker can steal the user information.Common cross-site scripting attacks can be divided into persistent and non-persistent cross station.
2 ATTACK CLASSIFICATION BASED ON WEB SERVICE
According to the different effects of attack methods,we can divide the classical attack technology into detection attack,authority attack,block attack and injection attacks[8],the classification results are shown in Fig.1.
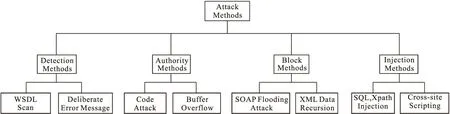
Figure 1 The Classification of Attack method
Since the attack effect is not the same,so the attack method,target,environmental constraints are not the same,the table 1 shows the different for each attack mode.
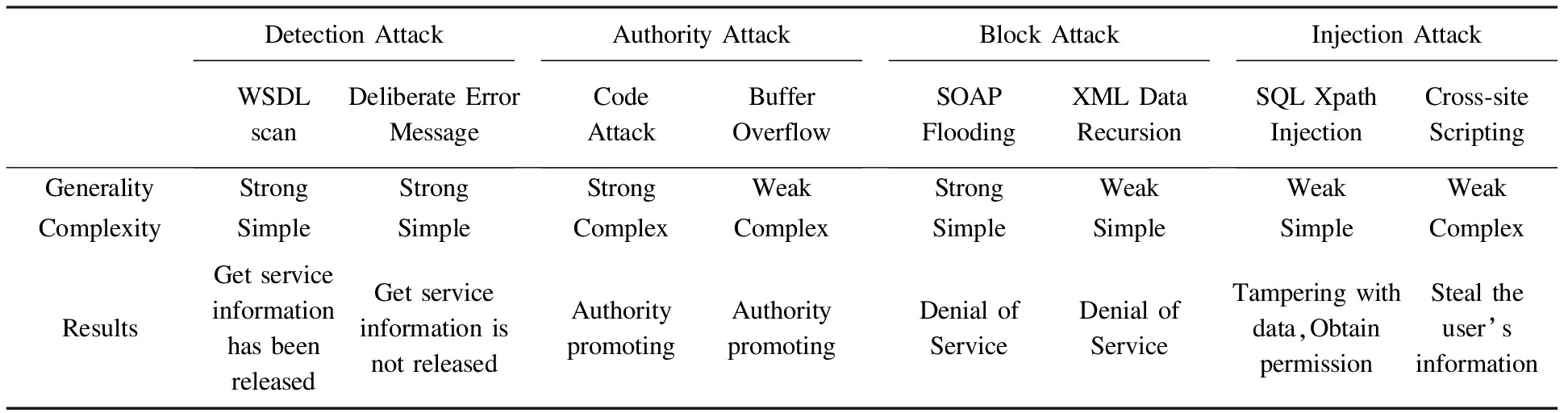
Table 1 COMPARISON AMONG THE CLASSICAL ATTACK METHODS
3 SIMULATION AND ANALYSIS
According to the attack methods cited above,the buffer overflow attack of the authority attack,the SOAP flooding attack and the XML recursion data attack of the block attack are simulated.The target server configuration is as follows:CPU Pentium (R) 4 CPU 3.06GHz,memory 2.49GB,windows XP Service Pack 3 system.
3.1 attack principle
1) the principle of Buffer Overflow attack
The existence of Buffer overflow attacks,is because some of the functions lack boundary detection mechanism,when the data that enter the buffer is over the length of the buffer’s capacity,the data that beyond the length will cover in the legitimate data,causing the program cannot continue to operate normally[9-10].When the attacker detect that the procedures exist in this kind of overflow,by constructing the shellcode,can make the programs execute the desired code,overflow attack core code is as follows:unsigned char eip[8]= JUMPESP;
unsigned char sploit[]=″/xEB/x10/x5A/x4A/x33/xC9/x66/xB9/xFF″
……
connect(sockFD,(structsockaddr
*)&server,sizeof(server));
strcpy(Buff+num1,(char *)eip);
strcpy(Buff+num1+4,(char *)sploit);
send(sockFD,Buff,strlen(Buff),0);
……
The shellcode can implement different functions,such as open port,reverse connection.After the success of buffer overflow attack,the attacker can connect to the server,and archive all the authorities of current user,Buffer overflow attack process is shown in Fig.2.
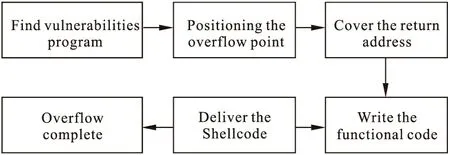
Figure 2 The Flow chart of Buffer Overflow attack
2) the principle of SOAP flooding attack
The existence of SOAP flooding attack is because the SOAP protocol itself only committed to the realization of a simple transmission,without adding any safety measures[11-12].The attacker can create the SOAP message that meet the requirement of Web service by analyzing the WSDL,or through the way of network monitoring,message structure is as follows:
POST /crazy/firstWS HTTP/1.1
Content-Type:text/xml;charset=UTF-8
Accept:*/*
SOAPAction:″″
User-Agent:Apache CXF 2.4.6
Cache-Control:no-cache
Pragma:no-cache
Host:10.166.178.123:8080
Connection:keep-alive
Content-Length:196
When the server receives a large number of duplicate SOAP messages,and all the messages meet the service’s requirement,so the server will deal with every pieces of the messages,resource consumption increased dramatically,while the remaining resource is insufficient,will reject the new message,resulting in denial of service.SOAP flooding attack process is shown in Fig.3.
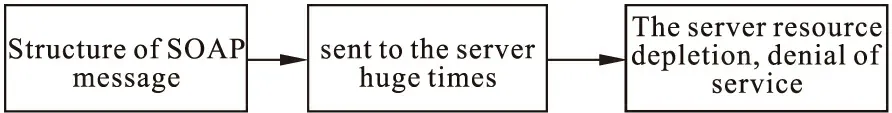
Figure 3 The Flow chart of SOAP flooding attack
3) the principle of XML data recursive attack
The existence of XML data recursive attacks is because XML allows for nested elements in a document,but there is no limit on the number and depth of recursive nesting,causing the attacker can increase the depth of nested XML data and send to the servers[13].XML data recursion structure is as follows:
……
When the servers are the lack of XML Schema to verify,the XML document will parsed,consuming a large amount of computation and memory resources,leading to service denial of service.XML recursion data attack process is shown in Fig.4.

Figure 4 The Flow chart of XML data recursion attack
3.2 analysis of simulation result
1) Result of Buffer Overflow attack
When the target servers are attacked by buffer overflow,the 11111 port will be opened.The remote attackers using Telnet to connect the host,access to the current user.Results are shown in Fig.5.
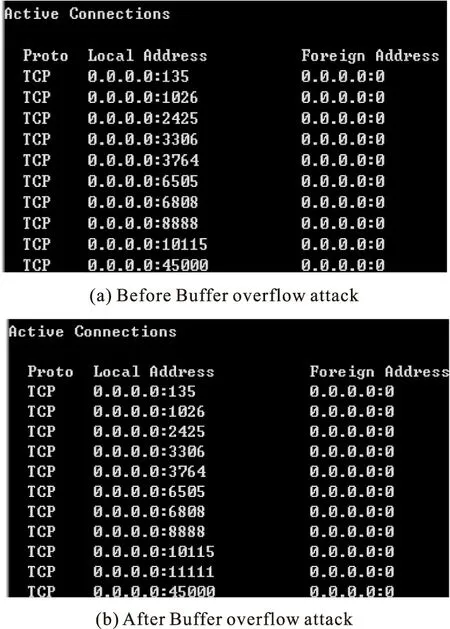
Figure 5 the Results of Buffer Overflow attack
From Fig.5 it can be see,the 11111 port was opened successfully after buffer overflow attack,and then,attackers can telnet target host with 11111 port,after the process of telnet,all privilege of target host can be achieved by attackers.
2) Result of SOAP flooding attack
SOAP flooding attack belongs to violence denial of service,the attack realizes by flooding a lot of messages,so both host resource and network resource changes obviously when under attack.When the target servers are attacked by SOAP flooding,a large number of computation and memory resources will be occupied,and network will be different flooding times will show different results.Results are shown from Fig.6 to Fig.8.
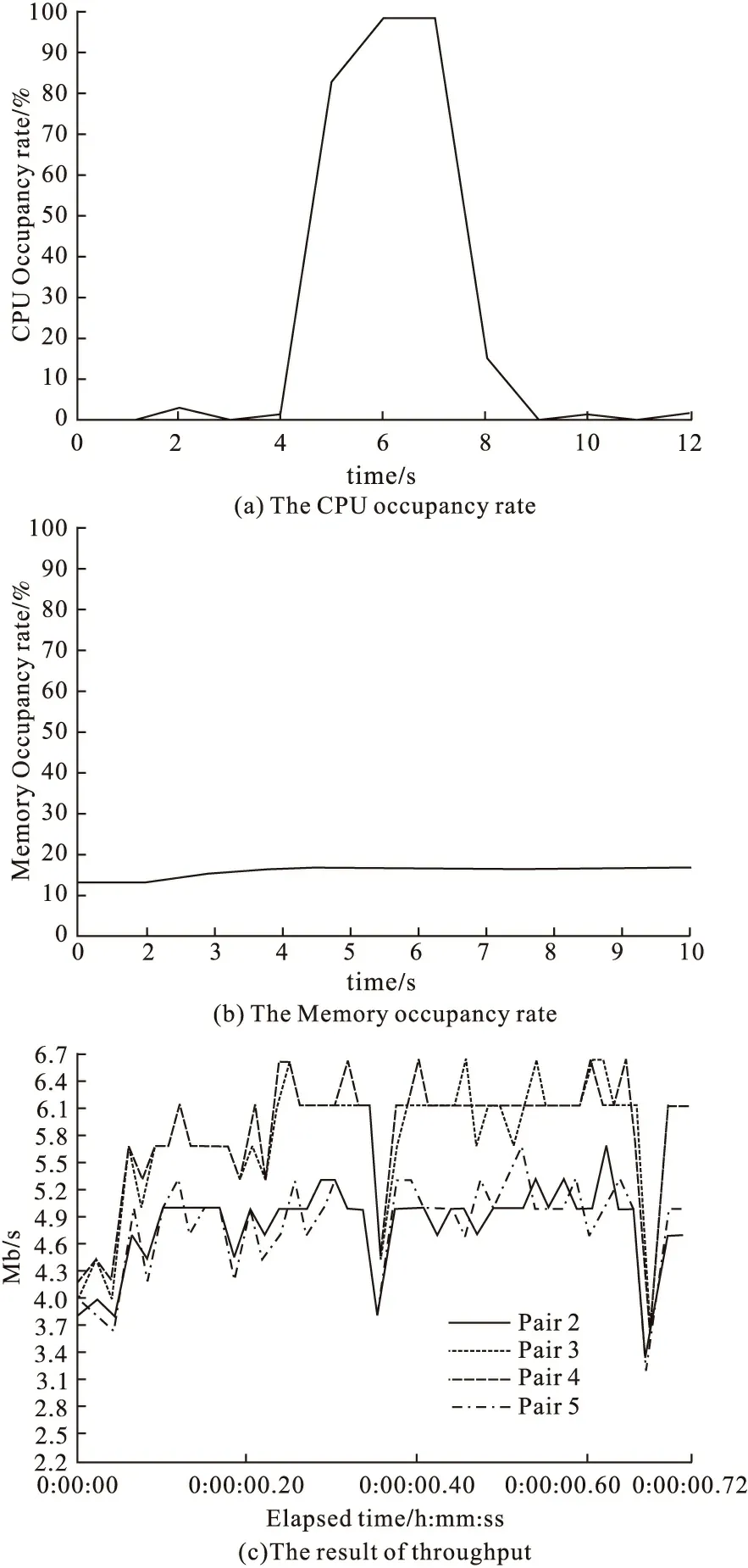
Figure 6 100 times of SOAP flooding attack
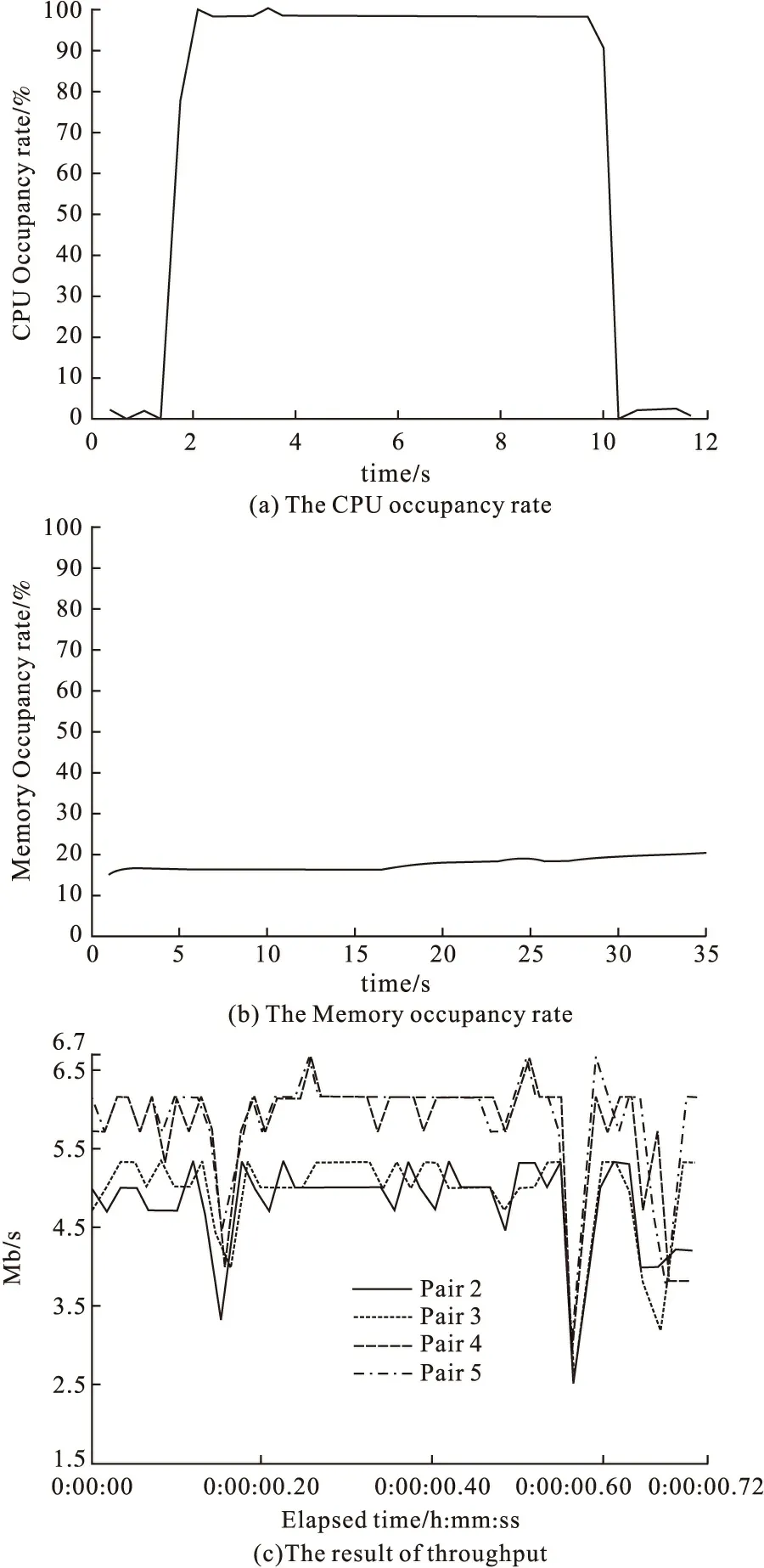
Figure 7 1000 times of SOAP flooding attack
Form Fig.6 to Fig.8,it can be seen that,with the increase of flooding times,the CPU occupancy rate and Memory occupancy rate increase evidently,it is because dealing with the messages has used huge number of computer resource and memory resource.Network resource also changes obviously.Though the max transmission speed for different times of SOAP flooding are same,but from throughput figure it can be seen that the minimum transmission speed has reduced with the increase of flooding times,because a number of messages that waiting to be deal will block transmission,so the host has to reduce transmission speed to ensure the integrality.In the process of one thousand and ten thousand times SOAP flooding attack,the host resulting in denial of service,as shown in Fig.9.
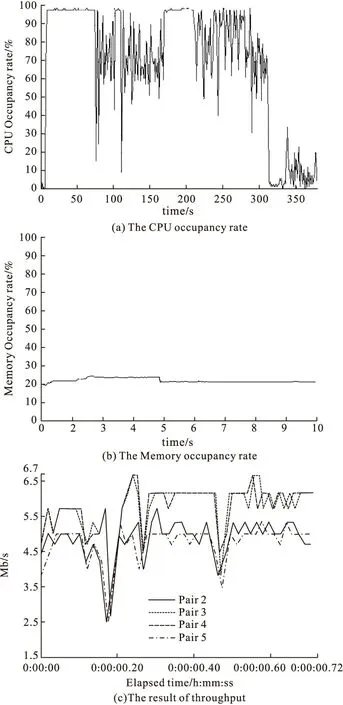
Figure 8 10000 times of SOAP flooding attack
3) Result of XML data recursion attack XML data recursion attack belongs to semantic denial of service,its attack process only need a key data package,but not a number of repeat messages,so it has no affection in network resource.The different recursion dept will lead to different data size after the key data package be parsed,so results are different when the host is attacked.Results are shown from Fig.10 to Fig.12.
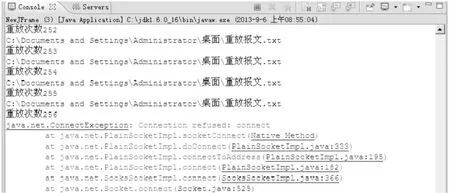
Figure 9 DoS under 1000 and 10000 times SOAP flooding
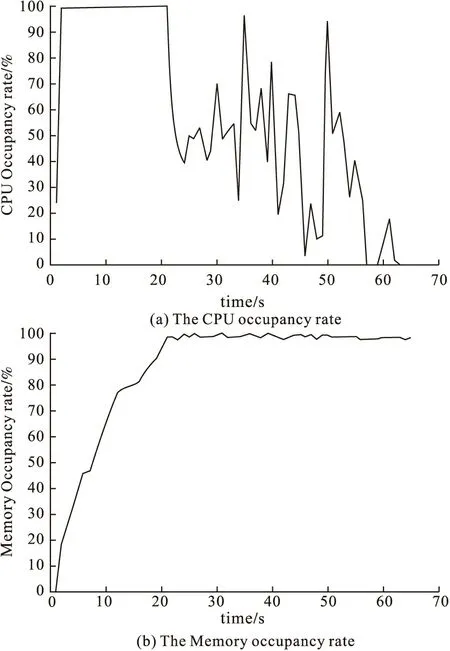
Figure 10 The Results of 1MB data recursion attack
From Fig.10 to Fig.12,it can be seen that with the increase of recursion dept,the data size will increase rapidly,so the CPU occupancy rate rise.It also can be seen that the memory occupancy rate is super higher than SOAP flooding attack,because the message will be parsed in the memory.In 100MB data recursion attack,the host appears some serious result such as computer halt,system resource crash,as shown in Fig.13.
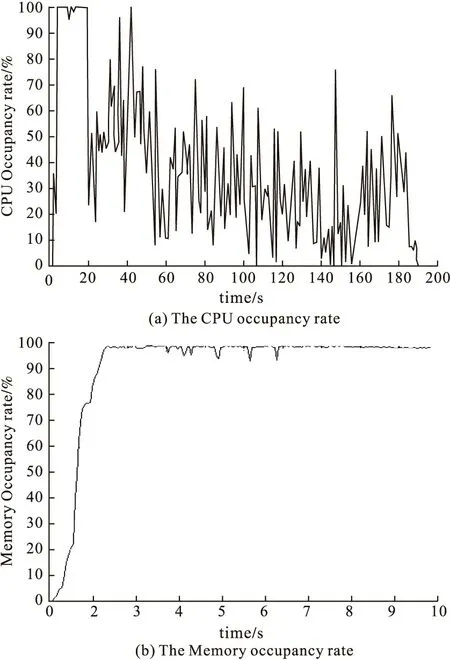
Figure 11 The Results of 10MB data recursion attack
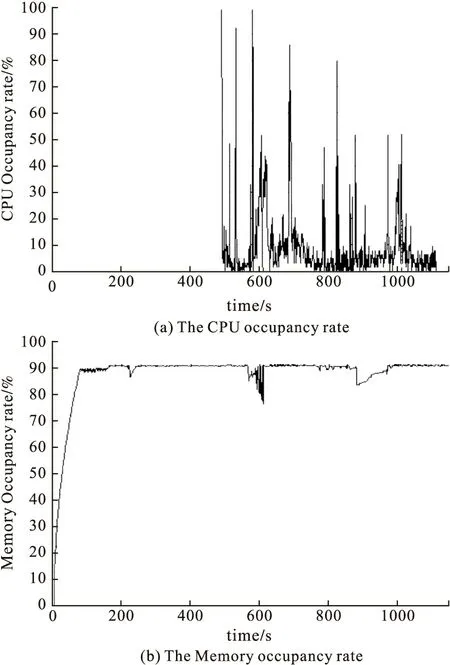
Figure 12 The Results of 100MB data recursion attack
Figure 13 IE crash under 100MB data recursion attack
4 CONCLUSION
According to the simulation results,the existence of buffer overflow attack is because the use of unsafe programming language,the existence of SOAP flooding attacks is because of flaws in the SOAP protocol itself,the existence of XML recursion attacks is because analysis of XML document lacks sufficient verification.
Therefore,in order to solve the security problems of Web service,the following need to be considered:1) To improve safety standards and specifications.This is the first problem to solve.Many organizations,such as IBM,W3C,OASIS,are constantly drawing new safety standards,issuing new safety regulations,in order to remedy the defects of the protocols.2) To formulate reasonable safety strategy.This includes many advanced strategies,such as identity recognition,access control,how can security problems at different levels to be solved in one strategy,is need to be further studied.In the formulation of the corresponding security strategy,not only for safety issues,transmission efficiency,and generality problem must be considered too.3) To upgrade security products.Products like firewalls,gateways have already solved the current safety problems,but with the development of technology,new vulnerabilities will appear,so the researches on security products also need continuous development.4) To develop new security technologies.Semantic Web services (Web3.0) has had the certain development in the technology and standards,but if the security problems cannot be solved,its application will be limited.Security technology development for the semantic Web will become the focus of future security study.
[1]Florije Ismaili,Bogdan Sisediev.Web Services Research Challenges,Limitations and Opportunities[J].WSEAS Transactions on Information Science and Applications,2008,5(10):1394-1403.
[2]Karp A H,Li J.Solving the Transitive Access Problem for the Services Oriented Architecture[C].IEEE International Conference on Availability,Reliability,and Security,2010:46-53.
[3]D.K.Smetters,R.E.Grinter.Moving from the design of usable security technologies to the design of useful secure applications[C].ACM New Security paradigms workshop,September,2002:82-89.
[4]HUANG Kangyua,HE Zhengqiua,LAI Hai-guang.Research of attack technologies for Web service[J].Application Research of Computers,2010,27(1):17-22.
[5]Kindy D A,Pathan A K.A survey on SQL injection:Vulnerabilities,attacks,and prevention techniques[C].2011 IEEE 15th International Symposium on.IEEE,2011:468-471.
[6]Feng Gu,Gao Peng.Research and Analysis of the Novel SQL Injection Technique[J].Computer Science,2012,39(11):415-417.
[7]Shashank Gupta,Lalitsen Sharma.Exploitation of Cross-Site Scripting (XSS) Vulnerability on Real World Web Applications and its Defense[J].International Journal of Computer Applications,2012,60(14):28-33.
[8]Wu Mingfeng,Zhang Yongsheng,LI Yuanyuan.Research of Web Services Attack Technology[J].Computer Technology and Development,2012,22(1):213-216.
[9]Rupasri M,Rajyalakshmi P,Sangeeta V.A Study of Buffer Overflow Attacks[J].International Journal of Engineering and Advanced Technology,2012,1(1):140-141.
[10]P.Vadivel Murugan,Dr.K.Alagarsamy.Buffer Overflow Attack-Vulnerability in Stack[J].International Journal of Computer Applications,2011,13(5):1-2.
[11]Khadijah Wan,Mohd Ghazaliand,Rosilah Hassan.Flooding Distributed Denial of Service Attacks-A Review[J].Journal of Computer Science,2011,7(8):1218-1223.
[12]Brajesh Kashyap,S.K.Jena.DDoS Attack Detection and Attacker Identification[J].International Journal of Computer Applications,2012,42(1):27-33.
[13]Haiping Xu,Abhinay Reddyreddy,Daniel F.Fitch.Defending Against XML-Based Attacks Using State-Based XML Firewall Kindy[J].Journal of Computers,2011,6(11):2395-2407.
