Application of Evolutionary Encryption 2D Barcode Generation Technology in Agricultural Product Quality and Safety Traceability System
2014-04-10XiaojunZHONGZhijieLAIYanCHENJianxinQIANXiaocongHONGCaiyiLI
Xiaojun ZHONG,Zhijie LAI,Yan CHEN,Jianxin QIAN,Xiaocong HONG,Caiyi LI
1.Guangdong Cuncuntong Science and Technology Co.,Ltd,Guangzhou 510663,China;2.Guangdong Science and Technology Information Center,Guangzhou 510033,China
A 2D barcode is a certain geometric graph distributed on black white plane(two-dimensional direction)according to certain rules.It is used to record data symbols.Researches of2D barcode technology started from the end of the 1980s.In the researches of 2D barcode technology,common codes include PDF417,QR Code,Data Matrix,Aztec,Maxicode,Code49,Code16K,Code One,Vericode,Ultracode,Philips Dot Code,and Softstrip,etc.Among these,QR Code,invented by Japanese Denso-Wave company,is the most common 2D barcode(Fig.1).

Fig.1 QR code
As a type of brand new information storage,transmission and recognition technology,2D barcode has received wide concern since its appearance.
1 Principle of 2D barcode encryption and evolutionary algorithm
1.1 Encryption methods for 2D barcodeAt the same time of wide application,2D barcode also brings about a series of safety problems.Due to data sensitivity,2D barcode needs higher safety.In this situation,it is particularly to study safe application of 2D barcode technology.At present,existing 2D barcode encryption technologies are mainly based on DES algorithm and Logistic chaotic algorithm[1-3].
1.1.1 DES algorithm based QR code encryption method.For this method,it firstly reads data of QR code image,then conducts encryption operation for black-white area in the 2D barcode with 64bitasunit using DES encryption algorithm.Finally,it combines unencrypted white area data and encrypted black-white area data and stores the data in the binary digital image format,and the stored image file is encrypted image data.
1.1.2 Logistic chaotic algorithm based QR code encryption method.Similar to DES algorithm based QR code encryption method,this method also firstly reads QR code image data,then assigns initial value and parameters that can generate chaotic sequence.Using
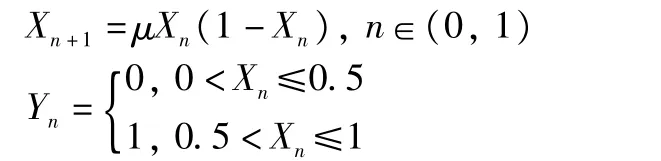
it generates Logistic binary chaotic sequence with a length of N×N.Finally,it conducts exclusive OR operation of binary image pixel of QR code,then converts BMP image format to realize encryption.
1.2 Principle of evolutionary algorithmEvolutionary algorithm(EA)is a subset of evolutionary computation,a generic population-based meta-heuristic optimization algorithm,inspired by biological evolution,such as reproduction,mutation,recombi-nation,and selection.In most applications of evolutionary algorithm,computational complexity is a prohibiting factor.In fact,this computational complexity is due to fitness function evaluation.Fitness approximation is one of the solutions to overcome this difficulty.However,seemingly simple evolutionary algorithm can solve complex problems.Thus,there may be no direct link between algorithm complexity and problem complexity.Evolutionary algorithm has self-organization,self-adaptation and self-learning characteristics.These characteristics make it have features of simple,easy operation and general use[4].
Steps of evolutionary algorithm include:
(i)Determining the coding scheme:generate population according to actual problem,represented by certain code of solutions.
(ii)Determining the crossover and mutation operations:using certain crossover and mutation operations to realize evolution of population.
(iii)Determining the fitness function:fitness is a measure of the quality of the solutions,usually constructed according to actual problem,and generally represented by objective function or cost function.The fitness is a decisive factor for selection of population.
(iv)Selecting control parameters:control parameters mainly include size of population,maximum algebra of algorithm,and some other auxiliary control parameters.
(v)Determining algorithm stopping rules:evolutionary algorithm is the process of constantly finding optimum solution in solution space.In the evolution process,it is possible to fall into partial optimum solution and fail to find real optimum solution and lead to infinite cycle of algorithm.Therefore,a common method is to define the condition for algorithm stopping when there is no obvious change in fitness value of the solution after a maximum evolution algebra or continuous substitution of algorithm.
(vi)Programming operation:the process of using certain programming language to realize specific evolutionary algorithm.
2 Evolutionary algorithm based 2D barcode generation algorithm
2.1 Algorithm thoughtBased on evolutionary encryption,in combination with evaluation strategy of image encryption,we control the encryption process through setting corresponding judgment threshold.It not only enhances safety of 2D barcode encryption,but also makes encryption and decryption controllable.
2.2 Realization of algorithm
2.2.1 Evolutionary algorithm based 2D barcode image encryption process.The input parameters include2D barcode image,initial encryption parameter and judgment threshold,and the output parameters are2D barcode image and iteration times.The specific process is illustrated in Fig.2.
(i)Input2D barcode image I and 64bit initial encryption parameter k before encryption,as well as corresponding judgment threshold F0,and initialize the iteration encryption times to zero,i.e.n=0.
(ii)Generate round key k1ik2ik3i…k64i required for encryption according to initial encryption parameter of64bit.
(iii)Process the 2D barcode image I before encryption by the crossencryption method,and record the2D barcode image obtained after cross encryption as I.
(iv)Conduct mutation encryption process for cross encrypted 2D barcode image I.Then,it finishes a complete round of evolutionary encryption process,record encrypted 2D barcode image as E,and add one to encrypted iteration times,i.e.n=n+1.
(v)For encrypted 2D barcode image E obtained in the above step,judge whether F satisfied judgment threshold condition according to corresponding evaluation indicator value F.If it satisfies the condition,the encryption process finishes,and the result image is the final2D barcode encryption image;if it fails to satisfy the judgment condition,assign the encrypted 2D barcode image E to I,return to step(ii),and continue to the next round of encryption.
In the above encryption process,the encryption key of algorithm includes initial parameter k and judgment threshold F0,etc.After each round of evolutionary encryption iteration finishes,it needs condition judgment.When it satisfies the condition,the encryption process finishes.This can guarantee that encrypted 2D barcode image satisfies evaluation rules.
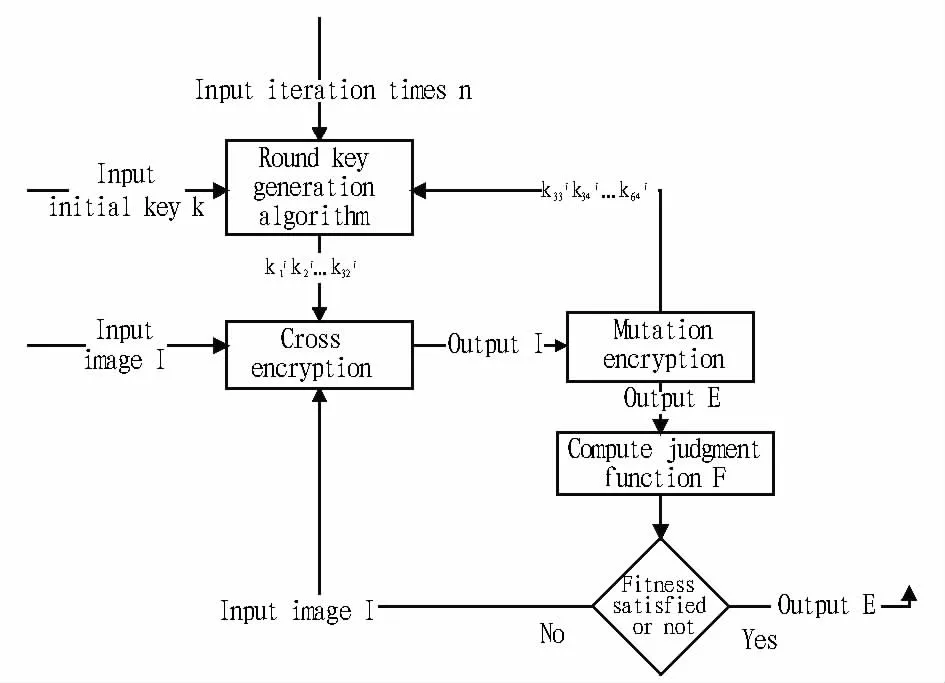
Fig.2 Process of encryption algorithm
2.2.2 Evolutionary algorithm based 2D barcode image decryption process.Firstly,it generates n groups of round key according to iteration times n of evolutionary encryption process.Next,use the round key in the sequence opposite to the evolutionary encryption.Finally,conduct decryption by the steps the same as encryption process.The decryption process is illustrated in Fig.3.
Input parameters for evolutionary algorithm based 2D barcode image decryption process include 2D barcode image E to be decrypted,initial decryption parameter k and encryption iteration times of encryption process.The decryption steps are as follows:
(i)Input the 2D barcode image E to be decrypted,initial decryption parameter k and encryption iteration times n of encryption process.
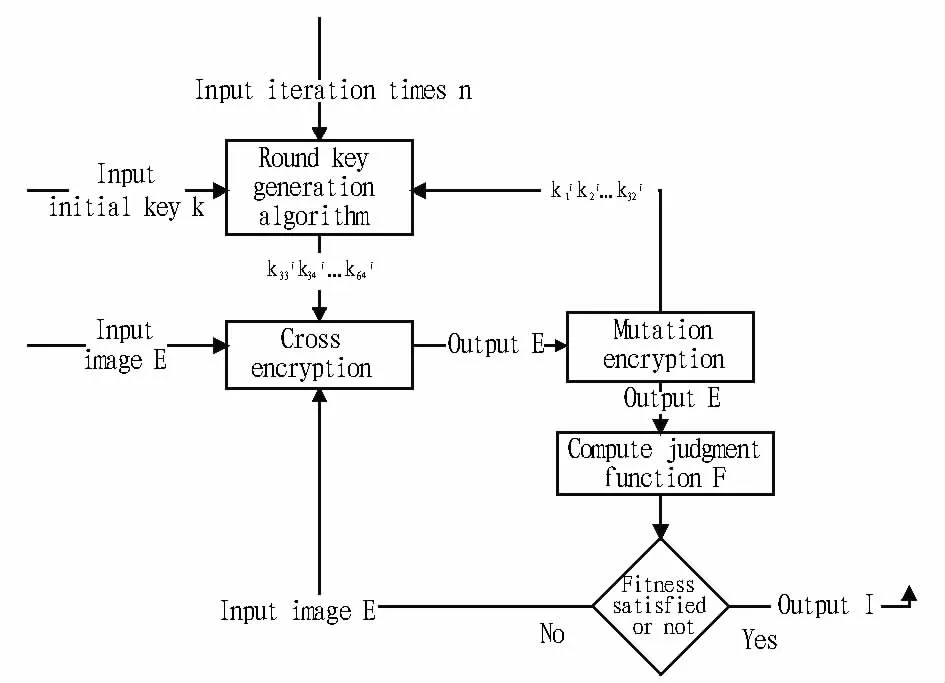
Fig.3 Process of decryption algorithm
(ii)According to decryption parameter k and n groups of round key k11k21k31…k641,k12k22k32…k642,…,k1nk2nk3n…k64n generated from encryption iteration timesn,use this round key in the opposite sequence.
(iii)Conduct mutation cooperation for 2D barcode image E to be decrypted and record the2D barcode image obtained through mutation decryption as E.
(iv)Conduct cross operation for 2D barcode image obtained through mutation decryption as E,perform a round of evolutionary decryption,and record the obtained 2D barcode image as E.
(v)According to iteration times n of encryption process,repeat the steps(iii)and(iv),and calculate to obtain the final decrypted 2D barcode image I.
2.3 Analysis on algorithmHere,we study the evolutionary algorithm based 2D barcode generation algorithm.The algorithm keys include initial parameter k and judgment threshold F0.According to the above description,since the initial parameter adopts 64bit,it is able to generate 64 groups of different round keys.Thus,it can guarantee safety of 2D barcode generation process.The judgment threshold is the key of another 2D barcode image generation process.Since the judgment threshold should be a value in a certain range,to make encryption iteration times change with judgment threshold,the value accuracy of judgment should be not less than 0.01.In this situation,the key of encryption algorithm should be larger than 264.This further guarantees safety of 2D barcode generation process.
3 Application of evolutionary encryption 2D barcode generation technology in agricultural product quality and safety traceability system
3.1 Application of2D barcode in agricultural product quality and safety traceability systemAs it is known to all,agriculture is the foundation of national economy.In recent years,frequent occurrence of agricultural product safety tests our life again and again."Sudan Red No.1"(2005),"melamine milk powder"(2008),and recent"lean meat powder","beef extract",and"tainted steamed buns"constantly threaten daily life and health of common people.Therefore,it is urgent to effectively realize follow up and trace agricultural products[5-9].
The agricultural product quality and safety traceability system is an information management system that can seamlessly connect agricultural product production process,inspection and quarantine process,supervision process and consumer links,let consumers know whether production and sales of agricultural products meet sanitation and safety,increase rights and interests of consumers.It can realize tracing from farmland to dining table.Once any problem found,it is able to realize effective recall of tracing process and safeguard lawful rights and interests of consumers.
With constant application and upgrade of2D barcode technology,traceability system combined with 2D barcode technology has been widely applied and used in agricultural product traceability system[10-14].Traditional 2D barcode only tags information and can not guarantee the safety,and information in 2D barcode is easy to be decrypted and forged.Therefore,to ensure safety of traceability system,the safety of2D barcode has become an essential problem.This study is based on evolutionary algorithm to realize encryption of 2D barcode,and applies encrypted 2D barcode into agricultural product quality traceability system,to further ensure safety of agricultural product traceability system.
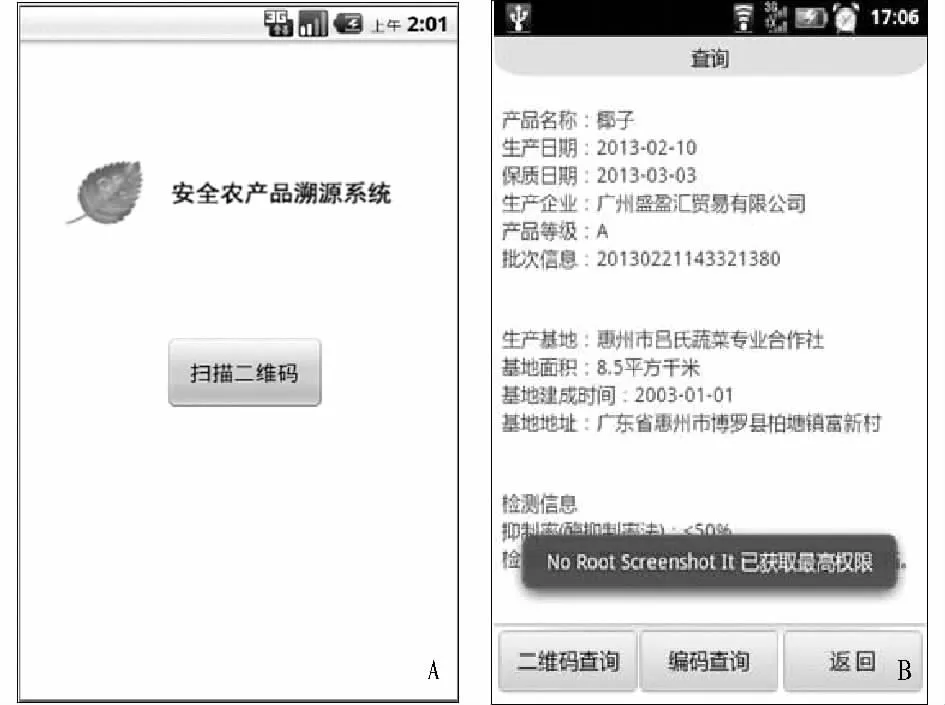
Fig.4 The mobile phone client 2D barcode inquiry system
3.2 Examples of application of evolutionary encryption 2D barcode generation technology in agricultural product quality and safety traceability systemWe selected 11 agricultural enterprises,including Guangzhou Institute of Agricultural Science,Guangzhou Riyuexian Agricultural Product Trade Co., Ltd,Shenzhen Zhongjian Vegetable Industrial Supply Chain Management Co.,Ltd in Cuncuntong Mall,realized tracing of safety of agricultural products from production level,and ensured food safety from circulation to dining table.It includes following modules:(i)issue of evolutionary encryption based 2D barcode,including generation of 2D barcode encryption and paste of encrypted 2D barcode;(ii)agricultural product traceability information management,including information inquiry of 2D barcode,producers of agricultural products,environment measuring of agricultural product bases,quality and safety inspection of agricultural prod-ucts,and circulation of agricultural products.
This platform encrypts 2D barcode image,so it is impossible to make decryption through general 2D barcode reading software,but needs special2D barcode reading equipment or log on safe agricultural product traceability system.Correct decryption process of this traceability platform is as follows:
(i)Through mobile phone.Firstly,download traceability system mobile phone client,install the client,open the software,you can see a button,as shown in Fig.4a.Scanning2D barcode of agricultural productusing mobile phone,the client will upload the 2D barcode to traceability platform background inquiry system,then feedback the inquiry result to the client,as shown in Fig.4b.
(ii)Through website.Firstly,log on the safe agricultural product traceability system platform,as shown in Fig.5a.In 2D barcode image upload area,click and upload 2D barcode image to be inquired.The website background will conduct decryption operation through input2D barcode image data,feedback inquiry result to user,as shown in Fig.5b.

Fig.5 Website client inquiry system
4 Conclusions and application prospects
Since the traditional QR 2D barcode generation method is difficult to ensure safety of 2D barcode information,we applied evolutionary encryption method into generation of 2D barcode.This effectively avoids data leakage due to human factor to a certain extent,greatly increases safety coefficient of 2D barcode,and guarantees safety and anti-counterfeit of 2D barcode.We applied this algorithm into actual agricultural product safety traceability system and proved that it is feasible and effective.
Information technology plays an irreplaceable role in safety of agricultural products,and wide application of information technology will bring China's agricultural product quality and safety system into information times.It is expected that through application of evolutionary algorithm based 2D barcode in agricultural product quality and safety traceability system,supervision authorities and consumers can conveniently and effectively know production environment of agricultural products and use of pesticide and chemical fertilizer.Therefore,from production to consumption,it can realize whole process supervision,information collection and issue of agricultural product circulation,and protect rights and interests of consumers.Besides,it can greatly promote optimum integration of supply chain of agricultural products,increase farmers' income and boost industrial development.
[1]ZHANG DH,SHAN JT,JIANG P.QR code DES encryption and decipher[J].Data Communications,2011(3):40-42.(in Chinese).
[2]ZHANG DH,GUO JB,JIANG P,et al.Encryption and decipher of QR code binary images chaos[J].Mobile Communications,2011,35(3):131-134.(in Chinese).
[3]WEIBD,LIU DS,WANG XM.The principle,implementation and cryptanalysis of AES algorithm Rijndael[J].Communications Technology,2002(12):65-68.(in Chinese).
[4]ZHAO F,JIAO LC,LIUHQ,et al.A novel fuzzy clustering algorithm with non local adaptive spatial constraint for image segmentation[J].Signal Processing,2011,91(4):988-999.
[5]CHEN LL,ZHUQJ,WANGWM,et al.The status,problems and countermeasures of agriculture products quality safety in China[J].Farm Products Processing,2010(3):58-59,64.(in Chinese).
[6]XINGWY.The policy of traceability in quality and safety of agricultural products in USA[J].World Agriculture,2006(4):39-41.(in Chinese).
[7]QIYM,LIXZ,GUO LY.Investigation of establishment and application of agricultural product safety management information system in foreign countries[J].World Agriculture,2009(5):10-13.(in Chinese).
[8]XIE JF,LU CH,LIBM,et al.Implementation of pork traceability system based on.NET framwork[J].Transactions of the Chinese Society of Agricultural Engineering,2006,22(6):218-220.(in Chinese).
[9]YANG XT,QIAN JP,SUN CH,et al.Design and application of safe production and quality traceability system for vegetable[J].Transactions of the Chinese Society of Agricultural Engineering,2008,24(3):162-166.(in Chinese).
[10]YANG XT,SUNCH,QIAN JP,et al.Construction and implementation of fishery product quality traceability system based on the flow code of aquaculture[J].Transactions of the Chinese Society of Agricultural Engineering,2008,24(2):159-164.(in Chinese).
[11]DENG XF,LV XN,ZHENG SY,et al.GIS-based traceability system of agricultural product safety[J].Transactions of the Chinese Society of Agricultural Engineering,2008,24(2):172-176.(in Chinese).
[12]Balvay LM B.Traceability of beef production and industry in France.in computer and computing technologies in agriculture II,volume 3[A]The Second IFIP International Conference on Computer and Computing Technologies in Agriculture(CCTA2008)[C].Beijing,China.Springer-Verlag New York Inc,2009:896-899.
杂志排行
Asian Agricultural Research的其它文章
- Overview of Current Research Situations of Subsoiler
- The Problem s in Rural English Teaching and the Optimization Path:A Study Based on the Chinese General Social Survey Data
- Analysis of the Status Quo of the Sericultural Standard System in China and Its Future
- Food Supp ly Values and Their Factors of Three Pond Aquaculture Ecosystems:A Case Study of Shanghai
- The Distribution of Cu Content of Soil in Different Land Use Types in the Suburbs of Changchun City
- Research Advances on Marine Ecological Effect and Repairing Techniques of Coastal Mangrove Wetland
